Data Centre Security: Protecting Infrastructure from Physical and Cyber Threats
Data
Data Centre Security: Protecting Infrastructure from Physical and Cyber Threats
News
Keepit crowned a winner in 2024 Cloud Security Awards
Keepit, a provider of SaaS data protection solutions, achieved success in the 2024 Cloud Security Awards programme by being named a winner in the 'Best Security Solution for Data Management / Data Protection' category.
Now in its second year and with an expanded range of categories, The Cloud Security Awards programme celebrates the pivotal innovations in cloud-based security solutions from around the globe. In addition to the aforementioned success, Keepit was also a finalist in the 'Best in Information Security' category.
Speaking on the company's success, James Williams, CEO of The Cloud Awards, comments, “Keepit has successfully navigated all three rounds of judging during a rigorous selection process, impressing the judges with their innovation and commitment to keeping data and other assets safe, secure, and private. We look on with interest to see what Keepit has in store for its customers throughout the rest of 2024, and beyond. Many congratulations to them, and our other winners.”
Michele Hayes, CMO at Keepit, adds, “Keepit supports customers around the globe by future-proofing their security strategies. This accolade underscores our commitment to innovation, security and reliability, and further positions the company as a leader in the cybersecurity industry.”
Built for the cloud, the Keepit platform is designed for usability, security and scalability. With a user-friendly interface, robust data security, and the ability to adapt to the user's cloud environment, Keepit ensures the user's data is always accessible and protected.
The Cloud Awards is an international programme which has been recognising and honouring industry leaders, innovators and organisational transformation in cloud computing since 2011. The Cloud Awards comprises five awards programmes, each uniquely celebrating success across cloud computing, software-as-a-service (SaaS), cloud security, artificial intelligence (AI), and financial technologies (FinTech).
Winners are selected by a judging panel of international industry experts. For more information about the Cloud Awards, click here.
For more from Keepit, click here.
Simon Rowley - 13 May 2024
Data Centre Security: Protecting Infrastructure from Physical and Cyber Threats
Data Centres
News
3D LiDAR set to redefine data centre security
Enhancing physical security, especially perimeter intrusion detection (PID) at critical infrastructure sites like data centres, warehouses, airports and utilities, is increasingly crucial due to growing threats such as theft, protests, sabotage, terrorism and war.
In its latest whitepaper, Quanergy 3D LiDAR Solutions Redefining the Physical Security of Critical Infrastructure, global technology intelligence firm ABI Research forecasts the worldwide physical security market for LiDAR sensors will surpass three million total installations by 2030, with water infrastructure leading the segment. The yearly revenue opportunity will exceed $6 billion (£4.8bn) in 2030.
“Physical security, specifically PID, encompasses controlling access for both individuals and vehicles into secured areas, as well as preventing objects from being thrown or passed across perimeter boundaries. Moreover, physical breaches often precede cyberattacks, underscoring the importance of intrusion detection in combating cyberthreats,” explains Dominique Bonte, Vice President, End Markets, at ABI Research.
Current security offerings rely on cameras and/or radar struggle to effectively detect and track intruders, and produce numerous false alerts, leading to higher operating costs and alarm fatigue. ABI Research states that these legacy 2D technologies lack accuracy and perform poorly in low light and adverse weather conditions, resulting in missed events, increased liabilities, and high cost of ownership.
According to Dominique, “3D LiDAR offers robust, reliable, and high-precision detection and tracking employing mesh architecture at an overall lower total cost of ownership (TCO), allowing security personnel and critical infrastructure to increase the effectiveness, while reducing the cost associated with manned guard services.”
The whitepaper explores: a comparison of physical security technologies; key critical infrastructure markets; LiDAR case studies for physical security segments; physical security LiDAR market sizing and forecasts; and Quanergy LiDAR solutions for physical security
ABI Research believes that 3D LiDAR solutions will have a transformational impact on the physical security market, redefining how to protect vulnerable critical infrastructure.
“The unique characteristics of LiDAR in terms of detection accuracy and reliability, range and field of view, continuous tracking, ease of deployment, and privacy preservation make it the technology of choice for next-generation physical security solutions to protect a wide range of mission-critical assets in the utility, data centre, airport, and other critical infrastructure segments,” Dominique concludes.
For more information on how 3D LiDAR can take physical security of critical infrastructure to the next level, download the whitepaper by clicking here.
Simon Rowley - 1 May 2024
Cyber Security Insights for Resilient Digital Defence
Data Centre Security: Protecting Infrastructure from Physical and Cyber Threats
News
Infinidat innovation recognised for its cyber security credentials
Infinidat, a provider of enterprise storage innovations, has announced that its InfiniBox SSA II has been recognised by analyst firm, DCIG, as one of the world’s top cyber secure all-flash arrays (AFA) for enterprise storage.
This high ranking, which was revealed in the 2024-25 DCIG Top 5 Cyber Secure High-End All Flash Arrays Report, is based on independent research that DCIG conducted into the AFA marketplace, with an expanded focus on cyber storage resilience and recovery.
“The recognition of the InfiniBox SSA II as one of the top five cyber secure AFAs in the world validates that not only is Infinidat’s primary storage solution the fastest all-flash array with industry-leading ultra-low latency, but also an industry acclaimed solution for cyber resilient storage,” says Eric Herzog, CMO at Infinidat. “Ever since we delivered the ground-breaking capabilities of InfiniBox SSA with our InfiniSafe cyber storage software and our InfiniVerse platform, Infinidat has redefined cyber resilience and recovery for enterprise storage. With an unprecedented guarantee, our InfiniBox SSA II ensures that enterprises and service providers recover and restore data at near-instantaneous speed after a cyberattack, significantly reducing the impact of ransomware and malware and saving companies time and money.”
Cyber resilience is among the most important and highly demanded requirements of enterprises today to ensure exceptional cyber security and resist cyber attacks across the entire storage estate and data infrastructure. Infinidat’s InfiniSafe cyber secure capabilities in the InfiniBox SSA II innovation combines immutable snapshots of data, logical air gapping, a fenced forensic environment, cyber detection, and virtually instantaneous data recovery, which clocks in at less than one minute, guaranteed. Infinidat leverages artificial intelligence (AI) / machine learning (ML) to provide deep content-level scanning to identify compromised data. The InfiniBox SSA II creates a private network that is isolated for data validation, facilitating the critical step of identifying a clean copy of data for reliable, rapid recovery.
"Having a cyber secure all-flash array is a necessity for enterprises to protect data from cyber attackers and ensure the security of the entire storage infrastructure, as well as to maximise business benefits by automating and consolidating workloads onto a higher-performance all-flash platform," said Dave Raffo, Consulting Analyst at DCIG. "A legacy all-flash array without cyber security capabilities built into it is already outdated and a potential huge liability in today's world of continuous cyberattacks. Our list of the top five Cyber Secure High-End All Flash Arrays constitutes the future of enterprise storage. The InfiniBox SSA II has earned a top spot because of advanced cyber resilience features on its platform, coupled with the performance, scalability, 100% availability, and cost-effectiveness that enterprises need."
The InfiniBox SSA II is Infinidat's high-performance, all-flash array aimed at mission-critical workloads that demand the ultimate in real-world application performance. It is integrated with the InfiniVerse platform, which accelerates Artificial Intelligence for IT Operations (AIOps) to automate and streamline storage management, utilises AI-based predictive analytics, and enables easier management of hybrid cloud storage implementations.
In addition to creating a cyber secure enterprise storage infrastructure that is efficient and dynamic, the InfiniBox SSA II allows customers to not only have optimal application and workload performance, but also allow for substantial storage consolidation, transforming storage performance, providing superior reliability, and reducing CAPEX and OPEX. The SSA II delivers the same 100% availability, white glove service, and lower total cost of ownership that defines the industry acclaimed InfiniBox customer experience, the company states.
To read the DCIG report, click here.
For more from Infinidat, click here.
Simon Rowley - 25 April 2024
Cyber Security Insights for Resilient Digital Defence
Data Centre Security: Protecting Infrastructure from Physical and Cyber Threats
News
Storage must form the core of an enterprise cyber security strategy
By James ‘JT’ Lewis, Director of Channel Sales for EMEA and APJ at Infinidat
It’s no wonder that in PwC’s 24th Annual Global CEO Survey, leaders ranked cyber attacks second place amongst the most serious of all possible economic, social, political, business, and environmental threats. Ransomware attacks represented 12% of breaches of critical infrastructure in the last year.
Cyber security experts have estimated that global cyber crime costs will exceed 7.5 trillion Euros this year, according to CyberSecurity Ventures. Enterprises run on data and when it’s hacked or corrupted by cyber criminals, the disruption can topple an operation overnight, with multi-million Euro consequences.
The irony is that, if the fallout from a cyber attack happened that quickly, it may be less problematic to recover from. Remedial action should be started immediately and any damage minimised. The actual problem is much more insidious because when cyber attackers target an enterprise, they usually wait for almost six months before taking action. This increases their ransom power and without the right data controls, the victim’s only option may be to concede to whatever financial demands are being made. In that timeframe, their primary data, the live data your business operations depend on, could have been exposed to all kinds of criminal activity.
For this reason, enterprise storage has become a main target of cyber criminals for the most damaging and hard-to-detect ransomware and malware attacks. One reason why enterprises still get trapped is because a cyber security strategy tends to focus on keeping criminals out in the first place, rather than accepting that attacks will most likely happen and there is an impetus for having a watertight strategy. The wolf will definitely keep knocking and will get inside your house. So, what steps can you take?
Firstly, cyber security’s emphasis must widen, to address three areas - detection, resilience and recovery - and plug the vulnerability gap that cyber criminals have been exploiting. Combining resilience, which is the ability to instil defensive security measures to repel attacks; detection, which is the ability to know when data is corrupted and whether a known good copy of data is free of ransomware or malware; and recovery, which is the ability to bounce back and recovery with a known good copy of the data from cyber attacks, is the key to hardening storage infrastructure.
Converging cyber resilience, detection, and recovery on an integrated enterprise storage platform is an advancement over former siloed approaches that rely on disparate tools and technologies. It makes the cyber capabilities more air-tight and ensures a rapid recovery of data within minutes to thwart cyber criminals, nullifying ransom demands and minimising downtime or damage to the business.
There are some key features of enterprise storage that need to be in place to ensure cyber resilience against today’s cyber criminals, all of whom are highly skilled technology experts. These include ensuring the immutable nature of the data, recovered from a copy you can trust. Air-gapping to separate the management and data planes to protect the data. A secure forensic environment, to analyse the data thoroughly and ensure the fastest recovery speeds possible is critical.
Immutable snapshots allow the end user to roll back the clock and recover guaranteed, uncorrupted copies of their data, before the execution of any malware or ransomware code introduced by an attacker. Immutable snapshots ensure data integrity because they prevent data copies from being altered or deleted by anyone. Even internal systems administrators are locked out of immutable snapshots manipulation. The enterprise can be confident that any disruption or damage caused by the intrusion is minimal.
Logical air gapping adds a further layer of security, by creating a safe distance between the storage management layer and the immutable snapshots. There are three types of air gapping. Local air gapping keeps the data on premises, remote air gapping makes use of a remotely hosted system and hybrid air gapping combines the two.
Fenced forensic environments help speed up the recovery process by providing a secure area to perform a post-attack forensic analysis of the immutable snapshots. The purpose here is to carefully curate data candidates and find a known good copy. The last thing an enterprise wants after an attack is to restore data infiltrated with malware or ransomware.
Once these core elements are present within your storage infrastructure, the whole restoration can progress like clockwork. It’s why our focus as an organisation is dedicated to educating IT leaders about the need for a convergent, tripartite approach. One that combining cyber resilience, detection, and recovery on a single storage platform. Reliance solely on backups and preventing attacks is no longer enough to secure storage systems.
Isha Jain - 2 April 2024
Data Centre Security: Protecting Infrastructure from Physical and Cyber Threats
News
iC Consult announces partnership with Transmit Security
iC Consult, an independent consultancy, systems integrator, and managed services provider for identity-driven cyber security, has announced a ground-breaking partnership with Transmit Security, the innovator of identity verification and fraud prevention services, including market-leading orchestration, phishing-resistant authentication with true password-less MFA, passkeys and modern customer identity and access management (CIAM).
This partnership marks a significant milestone in the pursuit of enhanced cyber security measures and fraud prevention capabilities and is set to offer businesses robust, frictionless authentication experiences that exceed current compliance and security requirements.
Transmit Security has been recognised for its commitment to revolutionising the customer authentication process, eliminating the need for passwords, and thereby, significantly reducing the risk of fraud. The decision to partner with iC Consult stems from its unparalleled expertise in IAM solutions, global footprint in delivering cyber security solutions, and a shared vision for delivering superior cyber security solutions that cater to the evolving needs of businesses worldwide.
Transmit Security’s VP & GM EMEA, Phil Allen highlights, "iC Consult’s global reach and innovative approach to identity management programs make them the ideal partner to advance our shared goal of making digital interactions safer and more user-friendly."
Kaltrina Ademi, Director of Channel Sales EMEA, adds, "Partnering with iC Consult was a natural choice for us. Their expertise in IAM and commitment to excellence complement our mission to secure digital identities across the globe."
Andre Priebe, Chief Technology Officer at iC Consult, shares, "Transmit Security’s password-less technology is a game-changer for our clients, addressing the urgent need for more robust cyber security measures in today’s digital landscape."
Heiko Klarl, Chief Marketing and Sales Officer at iC Consult, remarks, "This partnership enhances our ability to deliver cutting-edge solutions that effectively combat cyber security threats and fraud, marking a significant step forward in our mission to protect digital identities."
Isha Jain - 25 March 2024
Data
Data Centre Security: Protecting Infrastructure from Physical and Cyber Threats
News
Pedab and Object First join forces for advanced Veeam data protection
Pedab and Object First have announced a partnership to provide Veeam customers with advanced data protection to reduce the risk of cyber threats like ransomware. This partnership brings together two companies with complementary expertise, including Pedab's strong knowledge of IT infrastructure and software solutions and Object First's innovative approach to immutable backup storage for Veeam.
Object First claims that it is known for offering the best storage for Veeam, provided as an out-of-the-box immutable backup storage appliance. It offers the last line of defense against disasters and ransomware, ensuring that data can be recovered quickly and completely, with minimal downtime.
Pedab will introduce Object First’s solution Ootbi (Out-of-the-Box Immutability) to the Northern European market. Ootbi can be deployed in 15min and supports up to 80VMs running locally, powered by Veeam Instant Recovery on a four-node configuration. The solution’s power is matched by its security. It offers object-based immutability with zero access to the root or the hardened Linux operating system by default—meaning data cannot be accessed, changed, or deleted.
Ootbi's storage environment is completely secured, validated, and third party-tested and comes preconfigured out of the box – no security expertise required. With Ootbi, businesses can safeguard their data with confidence, knowing that critical information remains secure and unchangeable, even in the face of evolving cyber threats.
“Ootbi by Object First is an important enhancement to Pedab’s portfolio of carefully selected providers. It ensures Pedab’s mission to continuously evolve our full-service solution offering to partners. With Ootbi we can now help Veeam partners provide peace of mind to their customers with an immutable onsite backup storage,” says Jesper Bartholdson, CEO of Pedab Group.
“We are excited to announce Pedab as our distributor in Northern Europe. With their extensive expertise in the IT industry, partnering with Pedab was an easy choice,” says Mark Haddleton, EMEA Channel Sales Director at Object First. “Together, we are committed to delivering secure, simple, and powerful backup storage for Veeam users, helping businesses stay one step ahead of ransomware threats.”
Isha Jain - 21 March 2024
Data
Data Centre Security: Protecting Infrastructure from Physical and Cyber Threats
News
Keepit provides fast targeted restore time after ransomware attack
Keepit, a global provider of cloud backup and recovery solutions, has announced the results available to organisations leveraging Keepit SaaS data protection. The results show Keepit solution provides organisations the ability to restore and recover backed-up data after a ransomware attack in a quick, efficient and accurate manner.
These findings stem from a recent study conducted by Forrester Consulting, which quantify the value of the world’s sole vendor-independent cloud dedicated to SaaS data protection. Keepit commissioned Forrester Consulting to conduct a Total Economic Impact (TEI) study and examine the potential return on investment (ROI) that enterprises may realise by deploying Keepit SaaS data protection.
The purpose of this study was to provide a framework to evaluate the potential financial impact of Keepit SaaS data protection on end users. To better understand the benefits, costs, and risks associated with this investment, Forrester interviewed four representatives with experience using Keepit. For the purposes of this study, it aggregated the interviewees’ experiences and combined the results into a single composite organisation that is represented as a manufacturing organisation with $2bn in annual revenue.
While ransomware attacks have become increasingly common and organisations face the risk of losing critical data, Keepit claims to offer strong protection, providing a crucial lifeline for recovering user data after cyber attacks or other events. With Keepit, information technology (IT) administrators can quickly find, restore, and save data. Additionally, the study also shows that its solution helps prevent the negative effects of ransomware attacks and saves time and money for IT teams, resulting in smoother, more time-efficient SaaS backup operations.
Benefit worth $819,100
According to the study, the Keepit solution limits the impact of a ransomware attack for the composite organisation by allowing it to recover and restore data quickly, preventing data loss and reducing downtime. This benefit is worth $819,100.
And, the study finds, “the time needed to restore the tier-one users is 90% lower than the time the composite would spend restoring its data without Keepit, which has been identified by interviewees to be at least three weeks.”
“We can prove it’s possible to significantly lower downtime during recovery from a ransomware attack. Lowering downtime is a sure-fire way to maximise return on your investment in a backup solution. Because it’s not a question of if an attack will happen, the question is how to bounce back when it does,” says Paul Robichaux, Microsoft MVP and Senior Director of Product at Keepit.
Three quarters of security decision-makers suffered a breach in the last 12 months, and in the study, Forrester research recommends, “Backups are the best insurance policy against an attack, but to be effective they need to be part of a planned and tested backup and recovery process.”
The study participants noted that their organisations planned for a disaster scenario in the event of a ransomware attack and were aware of the exposure risk and potential losses they could suffer as a result.
As a follow-up to the Forrester study, Keepit will be holding a webinar at 2pm EDT on 26 March, titled, ‘The ROI of Ransomware Recovery’. Hosted by Keepit’s Paul Robichaux, the webinar will feature guest speakers Brent Ellis, Forrester Senior Analyst, and Elia Gollini, Forrester Associate Consultant.
Key takeaways from the webinar will include:
Actionable insights and recommendations on how to address current gaps in disaster recovery planning
Insight into best practices for ensuring business continuity during a ransomware attack
Information about the return on investment (ROI) organisations have realised when deploying Keepit for ransomware recovery
To register for the webinar, visit the sign-up page here.
Isha Jain - 21 March 2024
Data Centre Security: Protecting Infrastructure from Physical and Cyber Threats
News
IT leaders rely on immutable storage as ransomware attacks skyrocket
Scality, a leader in reliable, secure and sustainable data storage software, has announced the results of a survey of 500 IT decision-makers across France, Germany, the UK and the US, to gain insight into the role immutable data storage plays in an organisation’s overall cyber security strategy.
Key findings reveal:
94% either already rely on immutable data storage or plan to implement it within the next 12 months, and an additional 2% plan to deploy it within the next three years.
69% consider immutable data storage essential to their corporate cyber security.
Only 12% of those who deployed immutable data storage say it is not essential to cyber security.
Results from the independent survey by Vanson Bourne demonstrate that IT leaders consider immutable storage as a must-have in the fight against cyber attacks. Ransomware threats are now understood by organisations to be inevitable. Reports show one in four organisations that pay a ransom never get their data back, and just 16% are able to recover without paying a ransom.
This reinforces the role immutable data storage plays as an essential last line of defence within a cyber security toolkit. With immutable storage, data cannot be deleted or modified once written, increasing data safety and ensuring organisations have the power to restore data with 100% accuracy in the event of a breach.
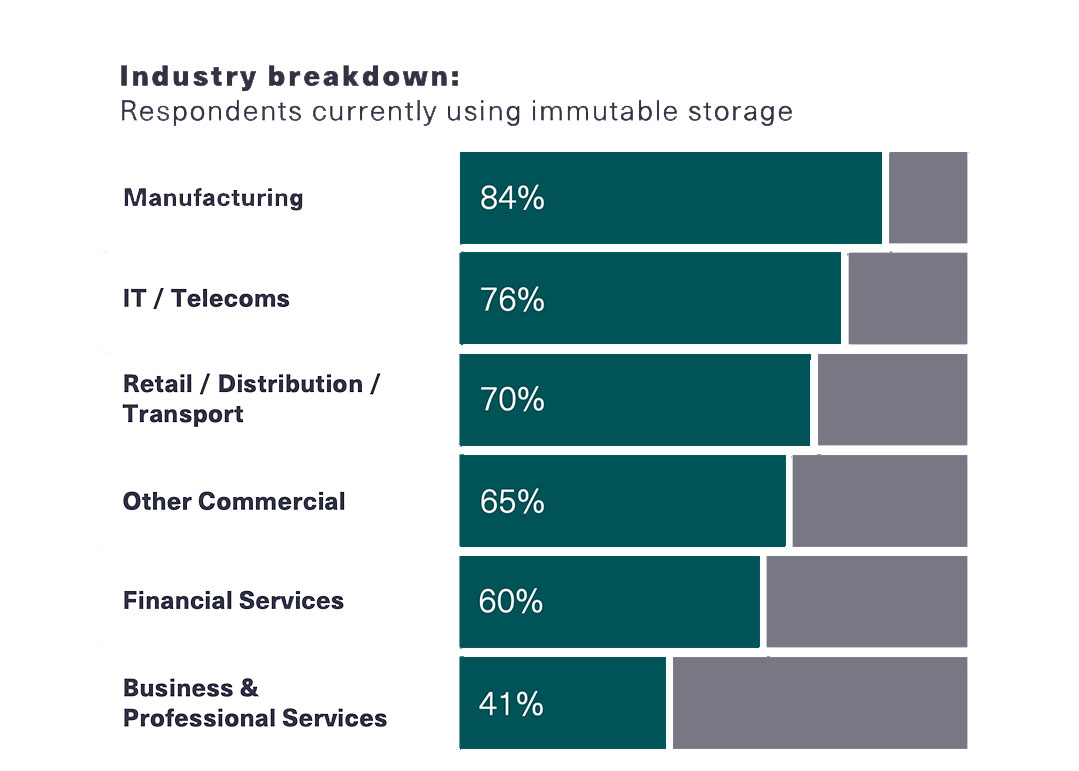
Survey insights: Vertical market and regional nuancesComparisons among IT leaders surveyed across vertical industries and specific countries reveal a number of notable differences:
Vertical market:
Manufacturing organisations (95%) are most likely to deploy immutable storage. While, 84% consider it essential to their corporate cyber security.
Financial services firms (74%) report the lowest reliance on immutable storage; 60% say it’s essential to their corporate cyber security.
Regional:
A majority of IT leaders across all regions currently use or plan to use immutable data storage: The US has the highest level of current or planned immutable data storage deployments, with 98% of respondents either having implemented it or planning to do so within the next year. This is followed by France at 96%, Germany at 94% and the UK at 85%.
While a relatively low number (12%) of IT leaders worldwide who currently use immutable data storage do not regard it as “essential” to their cyber security strategy, a larger percentage resides in the UK: 24% of UK respondents have deployed it but say it is not essential to their cyber security, compared to 11% in France, 9% in the US and 6% in Germany.
Dave Russell, VP of Enterprise Strategy at Veeam Software, says, “Widespread deployment of immutable storage reinforces an increased awareness of the critical role secure backup plays as an active defence against cyber attacks, specifically coupled with immutable backup data. Veeam believes that achieving zero trust data resilience with immutable storage implementations — that are indeed truly immutable — is a great opportunity for IT leaders to reduce the risk of growing data security threats and improve their overall cyber resilience.”
Does traditional immutable storage still leave a window of exposure?The survey reveals the criticality of immutable storage at a time of evolving industry dialogue about data cyber security best practices and technologies. But it’s important to note that not all immutability is created equal — some forms still leave a window of exposure.
Unlike forms of immutability enabled by traditional solutions - such as NAS/file system snapshots, dedupe appliances, Linux-hardened repositories or tape - true object storage solutions are inherently immutable at the core architecture level.
The system implements proper protocols and true object storage semantics to preserve data in its original form the very moment it is written, which is not the case for other immutable solutions that can introduce time delays before data is immutable. Each object, even those written nanoseconds apart, can never be overwritten, deleted, or modified. This architectural reinforcement provides a crucial last line of defence against ransomware attackers’ attempts to encrypt data and extort victims.
Paul Speciale, CMO, Scality, says, “Immutable data storage is an insurance policy against ransomware. While the survey data shows IT leaders resoundingly agree that immutability is a cornerstone of cyber security strategy, 31% still did not report it as essential. Here’s the reality: Being able to restore quickly from an immutable backup means the difference between a successful and unsuccessful ransomware attack. Without storage that’s truly immutable, you’re vulnerable to cyber criminals’ demands. The perception among some respondents that it’s not essential to cyber security is misguided and represents an opportunity to shift more IT leaders towards achieving a modern, inherently immutable object storage solution as a much-needed last line of defence to keep data locked and immune to ransomware exfiltration, modification or destruction.”
The survey was recently conducted by global technology market research firm Vanson Bourne across several industries, including manufacturing, telecom, professional services, financial services, and retail. Respondents were asked, ‘Is immutable data storage an essential element of your organisation’s corporate cybersecurity strategy?’ To qualify, each respondent carried a manager or above title in an enterprise-sized commercial organisation with over 1,000 employees and is primarily employed in the IT function.
Key findings in the UK:
85% of UK respondents currently rely on immutable storage or plan to implement it within 12 months. This is the lowest of the four regions (US, UK, France, Germany).
47% of UK respondents across all vertical markets consider immutable storage essential to their corporate cyber security strategy.
54% of UK respondents in the IT, technology and telecoms sector deploy and consider immutable storage essential to their corporate cybersecurity strategy. This is the highest score among all sectors surveyed in the UK.
Read the blog: What is true immutable storage?
Download the immutability checklist here.
Isha Jain - 15 March 2024
Data
Data Centre Security: Protecting Infrastructure from Physical and Cyber Threats
Neterra sees 100% increase in DDoS attacks blocked in 2023
Neterra has defended its clients from a record number of DDoS attacks in 2023. The company mitigated a total of 963,346 DDoS attacks and handled over 6.6PB of malicious traffic. Out of the total attacks, approximately 231,358 were of high intensity.
This marks a twofold increase compared to 2022, when the company thwarted 488,151 DDoS attacks.
Neterra employs a comprehensive approach to DDoS protection, combining cloud-based platforms, specialised hardware equipment, and other solutions. Through its specialised hardware equipment, the company halted 899,431 attacks, a significant portion of which were of high intensity and involved large volumes of malicious traffic. Neterra's cloud platform protected the company's clients from 63,915 attacks in 2023.
What Are DDoS attacks?
DDoS attacks typically manifest as a deluge of fake traffic, overwhelming the servers and websites of the targeted victim. Legitimate users are unable to access services, while hackers exploit the chaos to steal data. It can be likened to a massive crowd of fake customers blocking the entrance to a store, preventing genuine customers from entering.
What are the consequences?
DDoS attacks can result in financial losses, affecting online sales revenues, subscriptions, and advertising. They can also damage reputation by tarnishing the image and trust of clients, as well as lead to data loss — hackers may exploit the attack to steal sensitive information. This is the nature of a DDoS attack; an online tsunami that can last for days or even months, ultimately inundating any business.
DDoS attacks can result in financial losses, affecting online sales revenues, subscriptions, and advertising. They can also damage reputation by tarnishing the image and trust of clients, as well as lead to data loss, hackers may exploit the attack to steal sensitive information. This is the nature of a DDoS attack, an online tsunami that can last for days or even months, ultimately inundating any business.
Isha Jain - 8 March 2024
Data
Data Centre Security: Protecting Infrastructure from Physical and Cyber Threats
News
Acronis unveils Cyber Protect 16: A new era in cyber security
Acronis, a provider of cyber protection, has introduced the latest release of its flagship product – Acronis Cyber Protect 16. Acronis Cyber Protect delivers robust protection against cyber threats and unparalleled backup and recovery capabilities. This latest version establishes a new benchmark in easy and fast recovery after cyber attacks or data loss, especially for modern multi-site organisations.
As technology advances, the necessity for an integrated cyber security and data protection solution fit for distributed organisations has become increasingly evident. Factors including the rise of remote work and a rapidly changing threat landscape have increased attack surfaces and raised larger data access and privacy concerns. The product introduces a new centralised dashboard that further improves and simplifies management with a single pane of glass, providing visibility and simplified management for the entire environment.
Additional features of Acronis Cyber Protect 16 include:
Cyber threat protection: Using artificial intelligence (AI) and machine learning (ML), proactively secure data, applications, and systems from advanced cyber-attacks including ransomware and other forms of malware.
Rapid recovery: Reduced dependency on central IT support empowers users to initiate one-click recovery capabilities of distributed endpoints, including bare-metal recovery of physical workloads.
Reduced TCO: Broad, multi-generational OS support, enables vendor consolidation while ensuring comprehensive protection.
Simplified management: Centralised management includes local autonomy and seamless integration with existing third-party tools to provide a unified view of backup and recovery operations along with broad, multi-generational OS support.
Data sovereignty: With the use of Acronis’ extensive network of global data centres, users can ensure compliance and master regional data sovereignty laws, offering peace of mind and regulatory compliance.
“The release of Acronis Cyber Protect 16 underscores our dedication to protect all data, applications and systems,” says Gaidar Magdanurov, President at Acronis. “In today’s era of distributed environments, organisations require a cyber protection solution that provides reliable protection and fast and easy recovery after incidents. For many industries, like manufacturing, finance, healthcare, and retail, that can’t afford any downtime, it is crucial for non-IT personnel to be able to accomplish successful recovery; and that is what Acronis Cyber Protect 16 is bringing, one-click recovery after cyber attacks or data loss.”
Acronis Cyber Protect 16 provides a unique integration of backup, disaster recovery, cyber security, and remote endpoint management delivered via a single, cost-effective, efficient platform. With the ability to rapidly restore any computer without the need for IT intervention, specialised or industrial computing companies specifically in the operational technology (OT) industrial control systems (ICS) community, gain peace of mind and minimise costly downtime from potential outages. The integration of data protection, recovery capabilities, and advanced security functionality is designed to assure business continuity.
“With Acronis Cyber Protect, we offer our clients the peace of mind that comes with a true cyber resilience solution,” says Alan Conboy, Field CTO at Scale Computing. “We have complete confidence that if one of our customers suffers a cyber incident, we can get them back online in minutes. Acronis' single console seamlessly integrates comprehensive backup and recovery, endpoint management and cyber security to meet the needs of our broad range of customer environments, diverse OSs and organisational sizes. They are our go-to vendor to scale our business with world-class, affordable service offerings.”
Isha Jain - 21 February 2024

Head office & Accounts:
Suite 14, 6-8 Revenge Road, Lordswood
Kent ME5 8UD
T: +44 (0)1634 673163
F: +44 (0)1634 673173