Security Risk Management for Data Centre Infrastructure
Artificial Intelligence in Data Centre Operations
Data Centre Operations: Optimising Infrastructure for Performance and Reliability
Data Centre Security: Protecting Infrastructure from Physical and Cyber Threats
Security Risk Management for Data Centre Infrastructure
Vertiv launches AI predictive maintenance service
Vertiv, a global provider of critical digital infrastructure, has launched a new AI-powered predictive maintenance service, Vertiv Next Predict, aimed at modern data centres and facilities supporting AI workloads, including AI factories.
The managed service is designed to move maintenance away from time-based and reactive models, using data analysis to identify potential issues before they affect operations.
Vertiv says the service supports power, cooling, and IT systems with the aim of improving visibility and supporting more consistent infrastructure performance.
The company notes that, as AI workloads increase compute intensity, data centre operators are under pressure to maintain uptime and performance across increasingly complex environments. In this respect, predictive maintenance and advanced analytics are positioned as a way to support more informed operational decisions.
Ryan Jarvis, Vice President of the Global Services Business Unit at Vertiv, says, “Data centre operators need innovative technologies to stay ahead of potential risks as compute intensity rises and infrastructures evolve.
“Vertiv Next Predict helps data centres unlock uptime, shifting maintenance from traditional calendar-based routines to a proactive, data-driven strategy. We move from assumptions to informed decisions by continuously monitoring equipment condition and enabling risk mitigation before potential impacts to operations.”
AI-based monitoring and anomaly detection
Vertiv Next Predict uses AI-based anomaly detection to analyse operating conditions and identify deviations from expected behaviour at an early stage. A predictive algorithm then assesses potential operational impact to determine risk and prioritise responses.
The service also includes root cause analysis to help isolate contributing factors, supporting more targeted resolution. Based on system data and site context, prescriptive actions are defined and carried through to execution, with corrective measures carried out by Vertiv Services personnel.
According to Vertiv, this approach is intended to support earlier intervention and reduce the likelihood of unplanned outages by addressing issues before they escalate.
The service currently supports a range of Vertiv power and cooling platforms, including battery energy storage systems (BESS) and liquid cooling components. Vertiv says the platform is designed to expand over time to support additional technologies as data centre infrastructure evolves.
Vertiv Next Predict is intended to integrate as part of a broader grid-to-chip service architecture, with the aim of supporting long-term scalability and alignment with future data centre technologies.
For more from Vertiv, click here.
Joe Peck - 27 January 2026
Cyber Security Insights for Resilient Digital Defence
Data Centre Security: Protecting Infrastructure from Physical and Cyber Threats
Security Risk Management for Data Centre Infrastructure
Warnings of drone‑enabled cyber threats to critical infrastructure
As drone technology becomes more sophisticated and accessible across the globe, researchers from Innovation Central Canberra (ICC) at the University of Canberra have teamed up with Australian tech company DroneShield to understand the risk profile of cyber attacks to critical infrastructure.
With the rapid expansion of drone tech reshaping Australia’s security landscape, Defence, national security, and critical infrastructure are facing new challenges; meeting these requires capability that is not only technologically advanced, but also assessed and refined through rigorous, independent research environments.
“We know how drones have changed traditional warfare, but are we oblivious of the role they play in cyber security?" questions Professor Frank den Hartog, Cisco Research Chair in Critical Infrastructure at the University of Canberra. "That's a worry, and an opportunity for our drone and cyber industry.”
The project began with a team comprising Professor den Hartog and ICC students - namely Andrew Giumelli and Simone Chitsinde - undertaking targeted analysis and interviewing critical infrastructure operators to further understand the cyber threat environment through the use of drones.
Increasing threats to critical infrastructure
In the independent report, researchers found no recorded domestic cyber incidents using drones to date, but also noted that limited drone detection capabilities and awareness, minimal government guidance, and rising drone use are creating vulnerabilities.
This highlights a gap in reporting on drone-enabled cyber threats in Australia. The findings warn that the combinations of steadily increasing drone capability, limited awareness across industries, and a lack of targeted government guidance is creating a widening gap.
The report emphasises that drones are no longer emerging technology. Their capability, affordability, and accessibility have increased dramatically in recent years, and malicious actors are experimenting with drone-borne cyber techniques overseas.
Within the next five years, as drone and cyber capabilities continue to evolve, operators may need to reassess the likelihood and relevance of drone-enabled cyber threats.
Professor den Hartog continues, “This research highlights the need for greater education, more industry collaboration, improved knowledge sharing, and broader consideration of counter-drone capabilities across critical infrastructure sectors.
“We need to encourage operators to periodically and critically review how drones are used within their operations, assess the cybersecurity implications of increased adoption, and explore strategies to integrate drone risk into existing security and resilience programs.”
DroneShield’s engagement with ICC highlights the broader importance of research-industry collaboration in strengthening countries' sovereign capabilities. Acknowledging this, both organisations say they are exploring opportunities to continue the partnership.
Joe Peck - 22 January 2026
Cyber Security Insights for Resilient Digital Defence
Data Centre Security: Protecting Infrastructure from Physical and Cyber Threats
Security Risk Management for Data Centre Infrastructure
SIA launches data centre advisory board
The Security Industry Association (SIA), a trade association for global security solution providers, has launched a new Data Center Advisory Board to provide guidance on data centre security matters to its Board of Directors and to support SIA members with relevant resources.
The group will be chaired by Jim Black, Senior Director and Security Architect at Microsoft, who has been involved in the company’s cloud and data centre operations since 2011.
The establishment of the advisory board comes as global demand for data centre capacity continues to rise, driven by artificial intelligence, cloud services, and other digital technologies.
As facilities that host large volumes of sensitive information, data centres face increasing pressure to maintain robust and resilient security practices.
A focus on collaboration and guidance
According to SIA, the Data Center Advisory Board will contribute to the development of guidance and information related to security deployments, encourage collaboration between security providers and data centre security professionals, and engage with SIA’s government relations team on legislative and regulatory matters where relevant.
In his role at Microsoft, Jim is responsible for defining security technology strategy to protect assets and personnel across a global portfolio of more than 400 data centres.
He holds several professional certifications, including Certified Protection Professional and Physical Security Professional from ASIS International, as well as Certified Information Systems Security Professional from ISC².
Commenting on his appointment, he notes, “The data centre industry is experiencing unprecedented growth and heightened risks driven by emerging technologies and global operational challenges.
"I am honoured to serve as SIA’s inaugural Data Center Advisory Board Chair and look forward to working with this accomplished group of industry experts to advance and publish modern security standards that will strengthen cloud critical infrastructure protection worldwide.”
Don Erickson, CEO of SIA, says Jim’s experience makes him well suited to the role, commenting, “The Data Center Advisory Board is an important venture for SIA, and we are very pleased that it will be able to benefit from Jim’s experience and expertise in data centre security from its inception.
“Jim has for many years been an enthusiastic and generous supporter of SIA, contributing to multiple groups and projects that have advanced the industry’s professionalism and knowledge base. We are excited about what the advisory board will accomplish under his leadership.”
Joe Peck - 5 January 2026
Data Centre Infrastructure News & Trends
Data Centre Security: Protecting Infrastructure from Physical and Cyber Threats
Innovations in Data Center Power and Cooling Solutions
Products
Security Risk Management for Data Centre Infrastructure
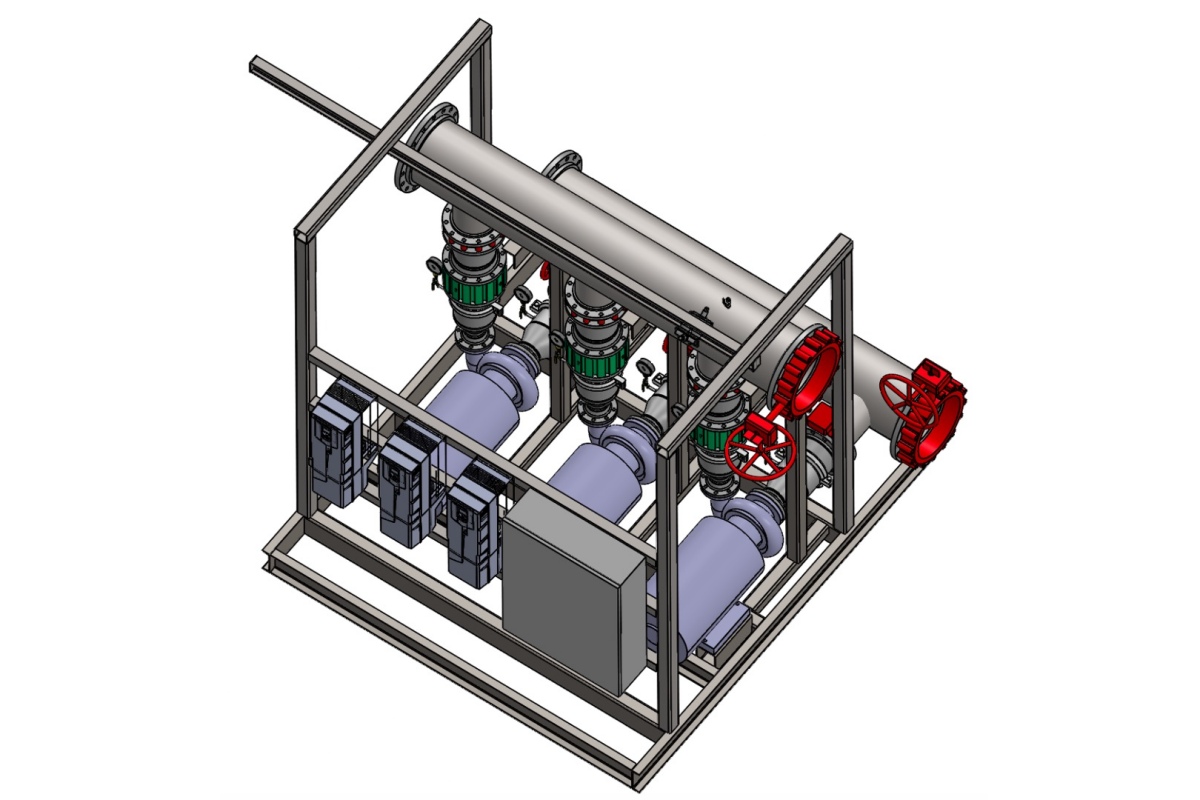
SPP Pumps brings fire and cooling experience to DCs
SPP Pumps, a manufacturer of centrifugal pumps and systems, and its subsidiary, SyncroFlo, have combined their fire protection and cooling capabilities to support the expanding data centre sector.
The companies aim to offer an integrated approach to pumping, fire suppression, and liquid cooling as operators and contractors face rising demand for large-scale, high-density facilities.
The combined portfolio draws on SPP’s nearly 150 years of engineering experience and SyncroFlo’s long history in pre-packaged pump system manufacturing.
With modern co-location and hyperscale facilities requiring hundreds of pumps on a single site, the companies state that the joint approach is intended to streamline procurement and project coordination for contractors, consultants, developers, and OEMs.
SPP’s offering spans pump equipment for liquid-cooled systems, cooling towers, chillers, CRAC and CRAH systems, water treatment, transformer cooling, heat recovery, and fire suppression. Its fire pump equipment is currently deployed across regulated markets, with SPP and SyncroFlo packages available to meet NFPA 20 requirements.
Integrated pump systems for construction efficiency
The company says its portfolio also includes pre-packaged pump systems that are modular and tailored to each project. These factory-tested units are designed to reduce installation time and simplify on-site coordination, helping to address construction schedules and cost pressures.
Tom Salmon, Group Business Development Manager for Data Centres at SPP and SyncroFlo, comments, “Both organisations have established strong credentials independently, with over 75 data centre projects delivered for the world’s largest operators.
"We’re now combining our group’s extensive fire suppression, HVAC, and cooling capabilities. By bringing together our complementary capabilities from SPP, SyncroFlo, and other companies in our group, we can now offer comprehensive solutions that cover an entire data centre's pumping requirements.”
John Santi, Vice President of Commercial Sales at SyncroFlo, adds, “Design consultants and contractors tell us lead time is critical. They cannot afford schedule delays. Our pre-packaged systems are factory-tested and ready for immediate commissioning.
"With our project delivery experience and expertise across fire suppression, cooling, and heat transfer combined under one roof, we eliminate the coordination headaches of managing multiple suppliers across different disciplines.”
Tom continues, “In many growth markets, data centres are now classified as critical national infrastructure, and rightly so. These facilities cannot afford downtime, and our experience with critical infrastructure positions us to best serve this market."
Joe Peck - 20 November 2025
Data Centre Infrastructure News & Trends
Data Centre Security: Protecting Infrastructure from Physical and Cyber Threats
Enclosures, Cabinets & Racks for Data Centre Efficiency
Products
Security Risk Management for Data Centre Infrastructure
R&M introduces radio-based access control for racks
R&M, a Swiss developer and provider of infrastructure for data and communications networks, is introducing radio-based access control for data centres. The core product is an electromechanical door handle for the racks of the BladeShelter and Freenet families from R&M.
Technicians can only open the door handles with authorised transponder cards, while administrators can control them remotely via encrypted radio connections and data networks.
R&M says it is thus integrating high-security digital protection into its "holistic infrastructure solutions" for data centres.
Package details
One installation comprises up to 1,200 door handles for server and network racks, as well as radio and control modules for computer rooms.
The door handles do not require any wiring in the racks. Their electronics are powered by batteries whose power is sufficient for three years of operation or 30,000 locking cycles.
The personalised transponder cards communicate with the door handles via RFID antennas.
In addition, there is software to manage users, access rights, the transponder cards, and racks. The software creates protocols, visualises alarm states, and supports other functions. It can be operated remotely and integrated into superordinate systems such as data centre infrastructure management (DCIM).
The new offer is the result of the collaboration with German manufacturer EMKA, being based on the company's 'Agent E', an intelligent locking system.
The R&M offering aims to integrate complementary systems from selected manufacturers into infrastructure for data centres.
In Europe, R&M notes it is already working with several independent partner companies that pursue comparable medium-sized business models and sustainability goals.
For more from R&M, click here.
Joe Peck - 18 November 2025
Data Centre Security: Protecting Infrastructure from Physical and Cyber Threats
Products
Security Risk Management for Data Centre Infrastructure
OPTEX introduces indoor LiDAR sensor for DC security
OPTEX, a manufacturer of intrusion detection sensors and security systems, has launched the REDSCAN Lite, a short-range indoor LiDAR sensor designed to provide precise and rapid detection for protecting critical infrastructure within data centres.
Founded in Japan in 1979, OPTEX has developed a series of sensor innovations, including the use of LiDAR technology for security detection.
The company says its REDSCAN range is recognised for improving the accuracy and reliability of intrusion detection in sensitive environments.
Addressing physical security risks in critical environments
As data centres across the UK and EU are now classified as critical infrastructure, operators face increasing pressure to meet strict security standards and mitigate both internal and external risks.
Industry data indicates that nearly two thirds of data centres experienced a physical security breach in the past year.
The REDSCAN Lite uses 2D LiDAR technology to detect intrusions within a 10 m x 10 m range, reportedly responding in as little as 100 milliseconds.
The sensor can be positioned vertically to create invisible ‘laser walls’ around assets such as server racks, ventilation conduits, and access points, or horizontally to protect ceilings, skylights, and raised floors.
Engineered for high-density environments, the REDSCAN Lite is capable of detecting small-scale activities such as the insertion of USB drives or LAN cables through server racks.
It is designed to operate effectively despite temperature fluctuations, low light, or complete darkness, helping reduce false alarms common in traditional systems.
Purpose-built for confined data centre spaces
Mac Kokobo, Head of Global Security Business at OPTEX, says the product was developed in response to growing demand from data centre operators, noting, “In today’s modern environments, such as data centres, spaces are becoming tighter and tighter filling with racks and processors.
"This latest REDSCAN Lite has been developed to meet the specific need for rapid detection in tight indoor spaces where high security is crucial.
“Feedback from customers highlighted a clear need for enhanced protection in small, narrow areas and spaces, so the REDSCAN Lite sensor has been designed to fit into the narrow gaps and is engineered to provide highly accurate and fast detection in indoor spaces that other technologies simply cannot reach.”
The REDSCAN Lite RS-1010L is now available for deployment.
Joe Peck - 12 November 2025
Data Centre Architecture Insights & Best Practices
Data Centre Build News & Insights
Data Centre Security: Protecting Infrastructure from Physical and Cyber Threats
News
Security Risk Management for Data Centre Infrastructure
AWS outage sparks call for resilient DC strategies
This Monday’s Amazon Web Services (AWS) outage demonstrates the importance of investing in resilient data centre strategies, according to maintenance specialists Arfon Engineering.
The worldwide outage saw millions unable to access popular apps and websites - including Alexa, Snapchat, and Reddit - after a Domain Name System (DNS) error took down the major AWS data centre site in Virginia.
With hundreds of platforms down for over eight hours, it was the largest internet disruption since a CrowdStrike update caused a global IT meltdown last year.
The financial impact of the crash is expected to reach into the hundreds of billions, while the potential reputational damage could be even more severe in the long run.
A preventable disaster
Although not caused by a lack of maintenance or physical malfunction of equipment and building services, the consequences of the downtime do reflect an opportunity for operators to adopt predictive maintenance strategies.
Alice Oakes, Service and Support Manager at Arfon, comments, “The chaos brought by Monday’s outage shows the sheer damage that can be caused by something as simple servers going down.
"While it might’ve been unavoidable, this is certainly not the case for downtime caused by equipment failures and reactive maintenance.
“This is where predictive maintenance can make a real difference; it's more resilient, cost-effective, and environmentally responsible than typical reactive or preventative approaches, presenting operators with the chance to stay ahead of potential issues.”
Predictive maintenance strategies incorporate condition-based monitoring (CBM), which uses real-time data to assess equipment health and forecast potential failures well in advance.
This enables informed and proactive maintenance decisions before the point of downtime, eliminating unnecessary interventions and extending asset life in the process.
CBM also reduces the frequency of unnecessary replacements, contributing to lower carbon emissions and reduced energy consumption in a sector under scrutiny for its environmental impact.
Alice continues, “This incident is a timely reminder that resilience should be built into every layer of data centre infrastructure, especially the physical equipment powering them.
"With billions set to be invested in UK data centres over the coming years, operators have a golden opportunity to future-proof their facilities.
“Predictive maintenance should be cornerstone of both new-build and retrofit facilities to adapt to ensure continuity in a sector where downtime simply isn’t an option.”
Joe Peck - 24 October 2025
Data Centre Build News & Insights
Data Centre Projects: Infrastructure Builds, Innovations & Updates
Exclusive
Security Risk Management for Data Centre Infrastructure
Pressing challenges impacting the future of US data centres
In this exclusive article for DCNN, Matt Coffel, Chief Commercial and Innovation Officer at Mission Critical Group (MCG), explores how growth in the US data centre market is being affected by increasing challenges, demanding new levels of collaboration and innovation across the sector:
An increasingly omnipresent industry
Data centres and related facilities are everywhere today. Synergy Research Group states hyperscalers account for 44% of those facilities worldwide, while non-hyperscale colocation and on-premise account for 22% and 34% respectively. They also project that by 2030, hyperscalers will account for 61% of all data centres and related facilities.
While there are no definitive estimates on how many of these facilities will be constructed in the US in the coming years, planning and development in the country are happening faster than ever before. Take, for example, the recent developments in Pennsylvania regarding investment in data centres and other technology infrastructure to support AI, including significant investments from Amazon and CoreWeave.
With AI adoption surging and data generation accelerating in sectors like healthcare, financial services, and the federal government, the number of data centres is only set to grow. But as demand rises, so too do the obstacles. Data centre operators and their partners face mounting challenges that threaten timelines, drive up costs, and complicate efforts to scale efficiently - and there are no easy fixes.
Persistent and critical challenges
When it comes to the construction of a data centre, there are many factors to consider. However, four factors have emerged as critical challenges for data centre operators and their partners: permitting, power, skilled talent, and compute.
1. Regulation: Securing permits to build and operate
Even as demand for compute and power accelerates, operators are forced to navigate lengthy and often inconsistent approval processes. In some jurisdictions, permitting can take two to three years before projects can even break ground. These delays put US developers at a disadvantage compared to countries with more streamlined regulatory systems.
The challenge is compounded by the sheer scale of today’s facilities. Projects promising multiple gigawatts of capacity require not only land and power, but also regulatory sign-off on issues such as environmental impact, emissions, and noise. These reviews often involve multiple parties - utilities, consultants, environmental specialists, and local governments - which makes coordination slow and uncertain. Moreover, the difficulty varies widely by location. In cities like Austin in Texas, approvals can be tough to secure, while just miles outside the city limits, the process may move much faster.
2. Time to power
According to the International Energy Agency’s (IEA) Energy and AI report, “Power consumption by data centres is on course to account for almost half of the growth in electricity demand between now and 2030 in the US.”
This rising demand is evident in Northern Virginia, where a large cluster of data centres has been built over the past twenty years. With this cluster of data centres in a single area, along with the demands from AI and data processing loads, power substations have reached maximum capacity. This has forced utility providers and data centre operators to either bring in new lines from distant locations - where there is excess power, but transmission infrastructure is lacking - or to build new data centres in rural areas so they can access untapped power.
Yet, building new transmission lines from other locations or setting up data centres can take years and doesn’t address the current power demand.
3. Access to skilled talent to support current and future projects
Data centre operators and their partners are working to build new facilities across the US, often in remote parts such as Western Texas, where they can access untapped power sources. Building in these areas introduces several challenges related to skilled labour.
Building and maintaining a data centre requires highly skilled electricians, mechanics, and controls specialists who can handle complex electrical and mechanical systems and often on-site power generation. However, the US faces a nationwide shortage of these workers. The US Bureau of Labor Statistics forecasts that employment for electrical workers will grow by 11% from 2023 to 2033 - a much faster rate than the average for all jobs. Still, many electricians are nearing retirement and set to leave the field in the coming years. This is likely to create a gap that operators will find difficult to fill as they work to build and keep their facilities running.
Additionally, data centre operators and their partners face the reality that many skilled workers are unwilling to live far from population centres.
Recent estimates from Goldman Sachs Research underscore the scale of this challenge. It projects that the US will require 207,000 more transmission and interconnection workers and 300,000 extra jobs in power technologies, manufacturing, construction, and operations to support the additional power consumption needs projected for the US by 2030.
This dual challenge of labour scarcity and logistical complexity is making traditional, on-site construction methods increasingly untenable. As a result, the industry is pivoting towards prefabricated, modular power solutions that are engineered and assembled in a controlled factory environment. This approach mitigates the impact of localised labour shortages by capitalising on a centralised, highly skilled workforce and deploying nearly complete, pre-tested power modules to the remote data centre location for rapid and simplified final installation.
4. The accelerating pace of change in compute technology
The speed at which compute technology is evolving has reached an unprecedented level, putting enormous pressure on data centre operators and their partners.
Moore’s Law is no longer the standard; today’s compute configurations are far more advanced than ever before, with denser platforms being released every 12 to 18 months. This rapid cycle forces operators to rethink how they design and future-proof facilities - leveraging concepts such as modularisation - as infrastructure built just a few years ago can quickly fall behind.
The need for collaboration
Each of these challenges is significant on its own, but together they mark one of the most complex periods in the history of infrastructure development. To move forward, data centre operators, utilities, manufacturers, technology providers, and government agencies must work closely to identify solutions and provide support for each obstacle.
On the skilled labour front, companies outside the manufacturing space are also contributing. Earlier this year, Google pledged support to train 100,000 electrical workers and 30,000 new apprentices in the US. This funding was awarded to the electrical training ALLIANCE (etA), the largest apprenticeship and training program of its kind, founded by the International Brotherhood of Electrical Workers and NECA.
State leaders are playing a role as well. In Pennsylvania this summer, for example, the governor and other legislators have demonstrated strong support for data centre growth.
MCG, a manufacturer and integrator of power and electrical systems, is one example of how industry players are stepping up. MCG designs, manufactures, delivers, and services systems tailored for data centre operators and other mission critical environments.
In collaboration with operators and other equipment and technology providers, MCG produces modular power systems that are built off-site to ease workforce constraints. These systems are then delivered directly to data centres or their power facilities, where the MCG team commissions and maintains them.
With efforts from government officials, companies like MCG and Google, and other stakeholders, the US data centre industry can continue powering the digital future - no matter how much demand for power and compute increases.
For more from Mission Critical Group, click here.
Joe Peck - 17 October 2025
Data Centre Infrastructure News & Trends
Data Centre Security: Protecting Infrastructure from Physical and Cyber Threats
Innovations in Data Center Power and Cooling Solutions
Security Risk Management for Data Centre Infrastructure
Sponsored
Uncover the hidden risks in data centre resilience
In July 2024, a lightning arrester failure in Northern Virginia, USA, triggered a massive 1,500MW load transfer across 70 data centres - handling over 70% of global internet traffic.
The result? No customer outages, but a cascade of grid instability and unexpected generator behaviour that exposed critical vulnerabilities in power resilience.
Powerside’s latest whitepaper - entitled Data Centre Load Transfer Event – Critical Insights from Power Quality Monitoring - delivers a technical case study from this unprecedented event, revealing:
• Why identical voltage disturbances led to vastly different data centre responses
• How power quality monitoring helped decode complex grid interactions
• What this means for future-proofing infrastructure in 'Data Centre Alley' and beyond
Whether you are managing mission-critical infrastructure or advising on grid stability, this is essential reading.
You can download the full whitepaper by registering below:
[ninja_form id=5]
Joe Peck - 13 October 2025
Cyber Security Insights for Resilient Digital Defence
Data Centre Security: Protecting Infrastructure from Physical and Cyber Threats
News
Security Risk Management for Data Centre Infrastructure
Securitas partners with Rohde & Schwarz on DC security
Securitas, a global security services provider, has announced a partnership with Rohde & Schwarz to integrate millimetre wave people-screening technology into its data centre security offering.
The collaboration is aimed at strengthening protection against insider threats, data theft, and sabotage as demand for always-on digital infrastructure increases.
Millimetre wave screening for critical environments
At the core of the partnership is the use of Rohde & Schwarz’s Quick Personnel Security Scanners (QPS), which employ millimetre wave technology and artificial intelligence to detect potential threats.
Already in use by government agencies and high-security organisations, the scanners provide non-contact, safe, and accurate screening while supporting real-time decision-making by on-site security officers.
According to Securitas, the QPS improves operational flow by reducing the need for manual screening, enabling more efficient staffing models and allowing remote monitoring. The system also provides insights into alarm rates and throughput, supporting both regulatory compliance and continuity of operations.
Milton Plet, Senior Vice President and Head of Global Clients Data Center Group at Securitas, says, “This is a perfect demonstration of how technology augments - rather than replaces - human expertise.
"Our officers are still at the core of the solution, only better supported by real-time information to make even better decisions in order to protect our clients’ assets.”
Expanding security options for data centres
Andreas Haegele, Vice President of Microwave Imaging at Rohde & Schwarz, adds, “The strategic partnership with Securitas enables us to introduce our security scanners, formerly exclusive to governments, now also to data centres, where adaptability, consistency, and precision are key.
"Together we are delivering a customised, future-proof solution that adapts to both clients’ needs and the threat landscape.”
Nelson Barreto, Senior Vice President, Global Clients at Securitas Technology, argues, “By combining electronic security expertise along with our global protective services and reach, we’re delivering a smarter, more adaptive approach to securing data centres, no matter where they’re located.”
Securitas has more than 90 years of experience in protective services. By adding advanced millimetre wave screening to its multi-layered security framework, the company says it aims to enhance both resilience and efficiency in data centre operations.
For more from Securitas, click here.
Joe Peck - 26 September 2025

Head office & Accounts:
Suite 14, 6-8 Revenge Road, Lordswood
Kent ME5 8UD
T: +44 (0)1634 673163
F: +44 (0)1634 673173