Data Centre Security: Protecting Infrastructure from Physical and Cyber Threats
Cyber Security Insights for Resilient Digital Defence
Data Centre Security: Protecting Infrastructure from Physical and Cyber Threats
News
NIS2 still a mystery to cyber security bosses, research shows
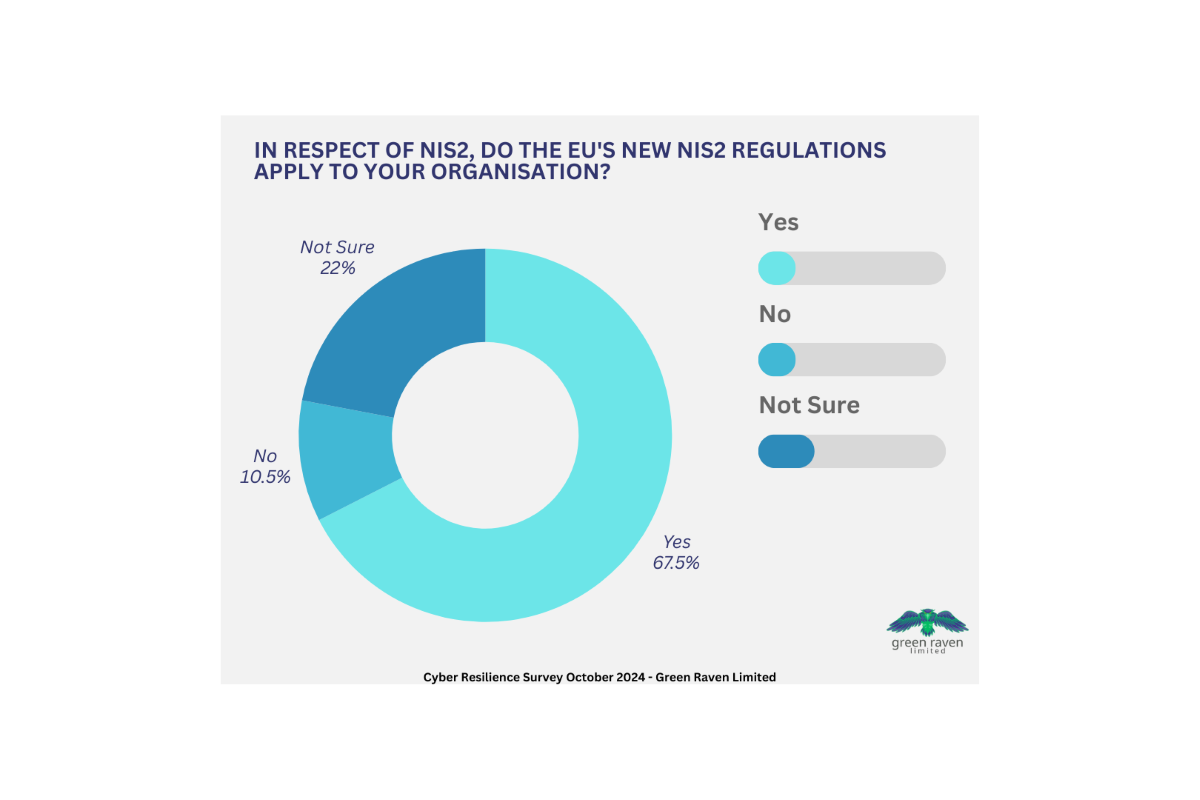
Senior cyber security professionals at more than a fifth of the UK’s largest businesses are still “not sure” whether the EU’s NIS2 directive - which is the EU-wide legislation on cyber security - even applies to their organisation, new research by specialist cyber security consultancy, Green Raven, has revealed.
More than two-thirds of respondents at organisations with at least 1,000 employees said that NIS2 does apply to them, but almost 10% of these admitted that their organisation was not compliant as of the 17 October 2024 deadline – with a further 3% not sure.
The findings contradict previous research from June 2024, in which 97% of IT leaders at UK companies declared themselves confident that they would be, or already were, NIS2-compliant.
Morten Mjels, CEO of Green Raven, says, “NIS2 came into force in January 2023 – almost two years ago – so for senior cyber security professionals at the companies most likely to be impacted to not know if it even applies - wow. Saying, 'Yes, we’re compliant' may be acceptable; admitting that 'No, we’re not compliant but we’re working on it' may also be acceptable - assuming there may be a grace period when new regulations come into force.
“But, eventually, failure to be compliant is going to significantly impact the ability of these organisations to do business in Europe, or is going to attract a significant fine for doing business in Europe without being compliant. And saying, ‘We weren’t sure’ is unlikely to be much of a defence.”
The research also asked respondents for their reaction to the Cyber Security and Resilience Bill, trailed by the UK Government in July 2024’s King’s Speech. This new bill is expected to build upon the foundations laid by the EU’s Network and Information Systems (NIS) directive and is commonly seen as the UK’s response to the NIS2 directive.
Asked to react based on what they had heard or read about the new Act:
• 37% of respondents hope that the new Cyber Security and Resilience Bill won’t apply to their organisation, but almost 80% expect that it will.• 46% of respondents expect the bill to make unwanted demands of UK businesses, but over 82% expected the bill to make reasonable demands of UK businesses. A similar proportion agreed that the bill would make necessary demands of UK businesses.• Almost 88% of respondents agreed with the statement "The UK Cyber Security and Resilience Bill will improve the UK's overall cyber resilience”. Not a single respondent disagreed with the statement, despite the acknowledgement of the additional demands and overheads the new bill is likely to bring.
Morten comments, “While few details are known beyond the idea that it will be the UK’s equivalent of NIS2, the key takeaway from the research is that every cyber security professional asked clearly believes that there is more that organisations can, and will, be forced – via legislation – to do to improve their cyber security posture and resilience. As a cyber security professional in an organisation likely to be in scope, I wouldn’t be waiting for legislation.”
Conducted on its behalf by research specialist, Censuswide, Green Raven surveyed 200 respondents from among the UK’s 1,930 organisations with at least 1,000 employees. All respondents described their role as CISO/director/head/manager of (or in) their organisation's cyber security team.
The EU’s Network and Information Security Directive (NIS2) aims to improve the overall level of cyber security and standardise cyber resilience across the EU, by requiring operators of critical infrastructure and essential services to implement appropriate security measures and report any incidents to the relevant authorities. EU member states were required to transpose NIS2 into their national legislation by 17 October 2024. Although the UK has left the EU, NIS2 impacts UK organisations that fall under its scope and conduct business in the EU, either as a customer or as a supplier.
Green Raven is a specialist cyber security consultancy and reseller, applying decades of track record, experience and knowledge to bring together customers and cyber security solution providers. In particular, Green Raven is a white-label partner for Darkscope, which is predictive cyber threat intelligence for enterprises. Green Raven’s implementation of Darkscope’s unique, AI-powered portfolio of solutions spots cyber attacks that others can’t, and before they take place – so those responsible for cyber security can reinforce their cyber defences where they know they’re about to be needed.
Its Supply Chain Monitoring Service leverages advanced cyber intelligence techniques and cutting-edge technologies to provide comprehensive oversight of an entire supply chain network – a key objective of the NIS2 directive.
Simon Rowley - 2 December 2024
Cyber Security Insights for Resilient Digital Defence
Data
Data Centre Security: Protecting Infrastructure from Physical and Cyber Threats
Data Privacy Insights for Secure Digital Operations
News
Zimperium predicts data privacy emphasis in 2025
Nico Chiaraviglio, Chief Scientist and Krishna Vishnubhotla, VP Product Strategy & Threat Intelligence at Zimperium, is predicting data privacy emphasis, more evasive phishing attacks and a rise of sideloading for 2025:
Each year around this time, security leaders cast their predictions on how the industry will change in the new year. What new threats will arise? How will organisations shift their security priorities? Which cybercriminal tactics will increase and which will decrease? At Zimperium, our mission is to secure the mobile attack surface and to empower security teams to effectively manage and mitigate mobile threats. In light of the research data we’ve compiled across millions of mobile devices and mobile apps over this past year, we’ve sat down to think about what new mobile security trends and threats you can expect to see in 2025.
Prediction 1: Mobile Security Platforms Will Increasingly Address Data Privacy Concerns, Not Just Security
Mobile security plays a crucial role in addressing the needs of data privacy. However, we often see mobile security with the lens of threat defence and application security. But regulatory compliance is a key piece of the mobile security function and we predict that in 2025, we will see mobile security prioritising data privacy needs by implementing robust privacy-preserving technologies.
According to Zimperium’s 2024 Global Mobile Threat Report, 82% of organisations allow bringing your own device (BYOD) to work. And a recent survey from Tableau found that 63% of Internet users believe most companies aren’t transparent about how their data is used, with 48% having stopped shopping with a company because of privacy concerns. We will likely see more regulatory compliance baked into mobile security solutions, particularly around data handling and encryption standards. We are already seeing regulatory shifts in the financial sector, holding app developers accountable for any harm towards their end users due to external attacks.
Businesses are recognising that regulatory compliance features are a necessary piece of the mobile security stack, and they are seeking mobile security platforms that address both privacy and security needs.
Prediction 2: Social Engineering Attacks Will Keep Becoming More Sophisticated and Evasive, Traditional Phishing Defenses Fall Short
Social engineering has evolved considerably over the past year. In 2025, we predict that 'mishing' (mobile phishing) attacks will become so sophisticated and evasive that traditional tooling won’t be able to detect it. We will see the rise of AI-driven mobile malware capable of mimicking user behaviour, making it far harder to detect using traditional methods.
Verizon’s 2024 Mobile Security Index revealed that AI technologies are expected to intensify the mobile threat landscape, with 77% of respondents anticipating AI-assisted attacks, such as deep fakes and SMS phishing. A notable example was identified by Zimperium’s zLabs researchers on an Android-targeted SMS stealer campaign, which to date, researchers have found over 107,000 malware samples directly tied to the campaign.
In separate research, the zLabs team found a new variant of the FakeCall malware, revealing new traits present in this variant, including the ability to capture information displayed on a screen using the Android Accessibility Service. Similar to the above, we will continue to see the development of 'stealth mobile devices', or devices specifically designed to circumvent typical security measures..
This highlights a strategic evolution in mobile security – evasive cyberattacks are now the new normal as cybercriminals are becoming more sophisticated in their mobile phishing attacks.
Prediction 3: Non-Traditional Entry Points Will Escalate Enterprise Mobile Risk
Threat actors will increasingly exploit iOS shortcuts, configuration profiles, and sideloaded applications to breach enterprise security. Recent research unveiled the dangers of sideloading applications, the practice of installing mobile apps on a device that are not from the official app stores.
According to Zimperium’s 2024 Global Mobile Threat Report, financial services organisations saw 68% of its mobile threats attributed to sideloaded apps. In fact, zLabs researchers found that mobile users who engage in sideloading are 200% more likely to have malware running on their devices than those who do not. Riskware and trojans, applications that disguise themselves as legitimate apps, are the most common malware families found.
APAC outpaced all regions in sideloading risk with 43% of Android devices sideloading apps. To protect against the risk that comes from sideloaded apps, enterprises must effectively protect their mobile endpoints by adopting a multi-layered security strategy including mobile threat defence and mobile app vetting.
The prominence of trojans are highlighted in the report with the findings indicating that threats from sideloaded apps are primarily driven by riskware and trojans, which account for a staggering 80% of the malware observed. Additionally, Zimperium’s threat data shows that approximately one in four Android devices face this issue. While sideloading is much more prevalent on Android, the recent Digital Markets Act (DMA) is expected to increase its prevalence on iOS.
Cybercriminals are constantly scouring for ways to break in and compromise corporate networks. In 2025, they will ramp up efforts on targeting non-traditional entry points.
Prediction 4: Surge in Mobile-Specific Ransomware
Mobile-specific ransomware is a rapidly evolving threat that should be top of mind for every CISO. Zimperium’s Mobile Banking Heist Report provides early evidence of this shift: in 2023, 29 malware families targeted 1,800 mobile banking apps with several showing early-stage ransomware capabilities. These tactics are tailored for mobile, signalling a move beyond data theft toward extortion and ransomware schemes designed specifically for mobile platforms.
This trend is part of a larger increase in ransomware and extortion attacks across digital channels. According to the 2023 Verizon Data Breach Investigations Report (DBIR), ransomware or extortion was involved in nearly one-third of breaches, indicating a shift among traditional ransomware actors toward new methods, including mobile-focused extortion.
This shift is further confirmed by the Thales 2024 Data Threat Report, which notes that ransomware and malware remain some of the fastest-growing threats, with 41% of enterprises facing malware-related breaches this year alone. With ransomware attacks growing by 21% in 2024, attackers are increasingly exploiting mobile platforms due to their unique vulnerabilities and often weaker security postures.
For CISOs, this signals an urgent need to prioritise advanced app-level security, phishing defences, and proactive monitoring in mobile environments, as the connectivity and sensitive data handled by mobile devices make them prime targets for the next wave of ransomware.
Zimperium’s zLabs research team is on a mission to identify emerging threats to mobile security, exposing malware groups and their variants before they have a chance to wreak havoc on businesses' mobile ecosystem. Our team will remain on the pulse of these developments, keeping a close eye on how these predictions play out in the new year.
Simon Rowley - 29 November 2024
Data Centre Security: Protecting Infrastructure from Physical and Cyber Threats
News
Macquarie Government expands Netskope partnership
Macquarie Government, part of Macquarie Technology Group, today announced it has expanded its four-year partnership with global SASE (Secure Access Service Edge) leader, Netskope, following a large-scale Federal Government network security deployment.
The Australian sovereign company deployed Netskope’s single-vendor SASE platform to the Department, ensuring it maintains compliance with the Essential 8 (E8) Maturity Model Level 2 controls. By adopting Zero Trust principles, the solution ensures all access is both explicitly requested and continuously revalidated, providing robust security measures critical for safeguarding government networks and data.
SASE architecture delivers an automated, dynamic policy enforcement framework, ensuring the Department’s personnel access applications securely based on their clearance levels, whether working remotely or on-premises. Without disrupting the user experience, SASE continuously verifies and validates access, blocking unauthorised data sharing on unapproved applications and guiding staff toward agency-approved tools, enhancing both security and compliance.
SASE underpinned by zero trust empowers Federal Government departments to embrace flexible working and complete cloud adoption – critical factors for attracting and retaining top talent. By enabling this modern workforce approach, it ensures robust security remains uncompromised, supporting the government's commitment to innovation and operational excellence.
As part of its strategic expansion, Macquarie Government was an early adopter and one of the first Australian organisations to be appointed to Netskope’s Managed Service Provider (MSP) Program. This milestone strengthens its capability to deliver advanced technology solutions to the Government, further cementing its role as a trusted partner in enhancing public sector security.
“The combination of Netskope's best-in-class single-vendor SASE platform with Macquarie Government's sovereign capabilities brings the promise of secure, flexible access to Australian Government agencies, transforming the way users and applications are secured,” says Aidan Tudehope, Managing Director, Macquarie Government (pictured above).
“By ensuring compliance with Essential 8 Maturity Level 2 standards, this partnership delivers enhanced security and resilience, providing a robust system that addresses the unique needs of government entities in an increasingly complex digital landscape.”
Tony Burnside, Senior Vice President and Head of APJ, Netskope, adds, “This deployment represents a significant milestone in advancing cyber posturing within the Australian Government. By leveraging the advanced capabilities of the Netskope One platform and Macquarie Government’s local engineering expertise, they have turned the vision of SASE into a practical, impactful reality.”
“Macquarie Government continues to refine their approach, delivering innovative solutions that enable SASE deployments at a PROTECTED classification while meeting the stringent compliance requirements of the Australian Government.”
This partnership expansion follows the addition of Macquarie Government to the Information Communications Technology Provider Arrangement (ICTPA) panel, enabling Australian Defence and Intelligence agencies to procure services directly from the company.
For more from Macquarie, click here.
Simon Rowley - 28 November 2024
Cyber Security Insights for Resilient Digital Defence
Data Centre Security: Protecting Infrastructure from Physical and Cyber Threats
Data Centres
News
DigiCert unveils 2025 security predictions
DigiCert, a global provider of digital trust, has released its annual forecast of cyber security predictions for identity, technology, and digital trust that the company expects to shape the landscape in 2025 and beyond. These predictions provide a snapshot of the cyber security challenges and opportunities enterprises will encounter in the months ahead.
Prediction 1: Post-quantum cryptography takes off2025 marks a pivotal year when post-quantum cryptography (PQC) shifts from theoretical frameworks to real-world deployments. With impending announcements from the US National Security Agency (NSA) and growing compliance pressures, PQC adoption will surge, empowering industries to embrace quantum-resistant solutions.
Prediction 2: Chief Trust Officers take centre stageDigital trust becomes a boardroom priority, leading to a continued rise of Chief Trust Officers (CTrOs) who will oversee ethical AI, secure digital experiences, and compliance in an increasingly regulated environment.
Prediction 3: Automation and crypto-agility become a necessityWith industry shifts toward shorter SSL/TLS certificate lifespans, automation and crypto-agility will emerge as critical capabilities for organisations aiming to maintain secure operations amidst evolving standards.
Prediction 4: Content provenance goes mainstreamIn an era of deepfakes and digital misinformation, the Coalition for Content Provenance and Authenticity (C2PA) is set to redefine how we verify digital content. Expect to see C2PA’s Content Credential icon become commonplace on images and videos to enhance trust across media platforms.
Prediction 5: Organisations will demand resilience and zero outagesThe CrowdStrike outage this summer underscored the need for better testing of automated updates and stronger digital trust. As IoT adoption grows, concerns about the safety of over-the-air updates, particularly for self-driving cars, are prompting calls for greater transparency in security practices. The EU’s Cyber Resilience Act, effective in 2027, will drive stricter cybersecurity standards, fostering a more secure and trustworthy IoT ecosystem.
Prediction 6: AI-driven phishing attacks will surgeThe proliferation of AI will fuel an unprecedented surge in sophisticated phishing attacks, making them harder to detect. Attackers will leverage AI to craft highly personalised and convincing phishing campaigns, while automated tools will enable them to scale attacks at an alarming rate, targeting individuals and organisations with precision.
Prediction 7: New private PKI standards like ASC X9 will gain momentumASC X9 is poised to gain momentum as industries like finance and healthcare increasingly require customised security frameworks to meet stringent regulatory demands and unique operational needs. Unlike public PKI, ASC X9 offers greater flexibility by enabling tailored policies and trust models, addressing critical areas such as data integrity and authentication. This ability to foster secure, scalable, and interoperable frameworks will make ASC X9 a preferred standard for organisations prioritising trust and collaboration.
Prediction 8: Cryptography Bill of Materials (CBOM) gains tractionIn response to escalating cyber security threats, CBOMs will become a vital tool for ensuring digital trust by cataloguing cryptographic assets and dependencies, enabling better risk assessments.
Prediction 9: The era of manual certificate management wndsManual management of certificates, still common in nearly a quarter of enterprises, will phase out as automation becomes indispensable for handling shorter certificate lifespans and stricter security protocols.
Prediction 10: Organisations will continue to prioritise fewer vendorsDespite concerns about single-vendor risks and a peak of venture capital funding for AI start-ups, enterprises will continue to consolidate vendors to simplify management, improve integration, and enhance overall security practices.
“The relentless pace of innovation is not just reshaping our digital lives - it’s exposing new vulnerabilities faster than we can secure them, demanding a bold rethinking of how we approach cyber security,” says Jason Sabin, CTO at DigiCert. “The predictions for 2025 underscore the urgent need to stay ahead of these vulnerabilities by driving quantum readiness, enhancing transparency, and reinforcing trust as the bedrock of our rapidly changing digital ecosystem. DigiCert remains committed to shaping and securing future digital innovation to remain ahead of the vulnerability curve.”
For more from DigiCert, click here.
Simon Rowley - 25 November 2024
Artificial Intelligence in Data Centre Operations
Cyber Security Insights for Resilient Digital Defence
Data
Data Centre Operations: Optimising Infrastructure for Performance and Reliability
News
AI security and data availability to underpin 2025 tech trends
AI has continued to be transformative throughout 2024, with accelerating adoption by enterprises and a growing number of use cases. According to experts from data platform, Nasuni, the AI boom will continue in 2025, but will be defined by three key pillars:
1. 2025 will bring a new era of security maturity - The ability to protect and quickly recover data assets underpins every other business process in an AI-first world
2. Data readiness will be central to AI success - As we look toward 2025, data will no longer just support AI, it will shape and limit the scope of what AI can achieve
3. Enterprises will strive to find the real ROI in AI - 2025 will usher in a more measured approach to AI investment, as organisations will be increasingly focused on quantifiable ROI
Discussing these predictions, Russ Kennedy, Chief Evangelist at Nasuni, says, “In 2025, data will be more valuable than ever as enterprises leverage AI to power their operations. However, as data’s value grows, so does its appeal to increasingly sophisticated threat actors. This new reality will continue driving organisations to rethink their security frameworks, making data protection and rapid recovery the backbone of any AI strategy. Attackers are evolving, using AI to create more insidious methods, like embedding corrupted models and targeting AI frameworks directly, which makes rapid data recovery as vital as data protection itself.
“Businesses will need to deploy rigorous measures not only to prevent attacks, but to ensure that if the worst happens, they can quickly restore their AI-driven processes. 2025 will bring a new era of security maturity, one where the ability to protect and quickly recover data assets underpins every other business process in an AI-first world.”
Jim Liddle, Chief Innovation Officer Data Intelligence and AI at Nasuni, comments, “As we look toward 2025, data will no longer just support AI – it will shape and limit the scope of what AI can achieve. A robust data management strategy will be essential, especially as AI continues advancing into unstructured data. For years, companies have successfully leveraged structured data for insights, but unstructured data – such as documents, images, and embedded files – has remained largely untapped. The continued advancements in AI’s ability to process the different types of unstructured data that reside within an enterprise are exciting, but they also require organisations to know what data they have and how and where it’s being used.
“2025 will mark the era of ‘data readiness’ for AI. Companies that strategically curate and manage their data assets will see the most AI-driven value, while those lacking a clear data strategy may struggle to move beyond the basics. A data-ready strategy is the first step for any enterprise looking to maximise AI’s full potential in the coming years.”
Nick Burling, Senior Vice President, Product at Nasuni, adds, “2025 will usher in a more measured approach to AI investment, as organisations will be increasingly focused on quantifiable ROI. While AI can deliver immense value, its high operational costs and resource demands mean that companies need to be more selective with their AI projects. Many enterprises will find that running data-heavy applications, especially at scale, requires not just investment but careful cost management. Edge data management will be a critical component, helping businesses to optimise data flow and control expenses associated with AI.
“For organisations keen on balancing innovation with budgetary constraints, cost efficiency will drive AI adoption. Enterprises will focus on using AI strategically, ensuring that every AI initiative is justified by clear, measurable returns. In 2025, we’ll see businesses embrace AI not only for its transformative potential, but for how effectively it can deliver sustained, tangible value in an environment where budgets continue to be tightly scrutinised.”
For more from Nasuni, click here.
Simon Rowley - 18 November 2024
Data Centre Security: Protecting Infrastructure from Physical and Cyber Threats
Enterprise Network Infrastructure: Design, Performance & Security
News
Singtel expands its suite of quantum-safe offerings
Singtel today announced that it will be enhancing its suite of quantum-safe offerings to help enterprises fortify their defences against cyber threats and scale more securely in the quantum age.
This involves integrating Post-Quantum Cryptography (PQC) technology, which is algorithms engineered to resist the computational power of attacks from quantum computers, from leading cybersecurity solutions providers, Palo Alto Networks and Fortinet, into Singtel’s nationwide Quantum Safe Network (QSN).
As part of the collaboration, Palo Alto Networks will protect against quantum threats with a PQC IPSec (Internet Protocol Security) virtual private network (VPN), using the new post-quantum encryption standards established by the US National Institute of Standards and Technology for secure data transmission and authentication.
Fortinet’s quantum-compatible solutions will integrate PQC and Quantum Key Distribution (QKD), which is a secure method for distributing encryption keys only known between shared parties, to support the development of a secure, scalable, and commercially viable QSN for Singtel. Singtel will leverage Fortinet’s quantum-resistant PQC software, hardware encryptors, and advanced platforms to build robust quantum-safe architectures and solutions tailored for enterprise needs. Together, these partnerships will ensure that encryption keys remain secure across diverse applications, including identity, mobility, and authentication services – creating a more resilient defence for enterprises against cyber threats.
Keith Leong, Managing Director, Enterprise, Singtel Singapore, says, “Quantum computing presents a significant threat to traditional encryption methods, and has the potential to disrupt our digital economy by potentially decrypting sensitive data, exposing businesses to significant risks. The addition of Palo Alto Network and Fortinet’s enhanced software solutions to our QSN ensures our enterprise customers get more industry-leading choices to secure their business against both current and future quantum threats, regardless of their hardware requirements. We encourage enterprises to take the necessary steps to secure their critical assets sooner rather than later.”
Steven Scheurmann, Regional Vice President of Palo Alto Networks in ASEAN, adds, “Quantum computing represents a revolutionary technology that promises tremendous advancements but also introduces potential risks, especially for data security. At Palo Alto Networks, we are committed to helping enterprises prepare for this future. By integrating our quantum-resistant VPN solutions with Singtel's Quantum-Safe Network, we're ensuring that customers can safeguard critical data against both current threats and encryption-breaking capabilities of future quantum computers. It's essential to take action today to secure tomorrow's digital landscape and we are proud to be part of Singtel's efforts to lead in this space.”
Jess Ng, Country Head, Singapore and Brunei, Fortinet, remarks, “As quantum computing evolves, so must our approach to cybersecurity. Fortinet is proud to collaborate with Singtel to strengthen the nation’s defences against emerging threats. By integrating Post-Quantum Cryptography (PQC) and Quantum Key Distribution (QKD) into Singtel’s Quantum-Safe Network, building hybrid architecture, and leveraging quantum-safe solutions, we are helping enterprises stay ahead of future risks. Through the development of industrial and government use cases, we are committed to building a foundation for a more resilient and secure digital future.”
Following the Infocomm Media Development Authority’s appointment last year to develop a nationwide QSN to fortify Singapore’s resilience against quantum threats, Singtel launched the nation’s first QSN with global leader in quantum-safe cryptographic solutions, ID Quantique (IDQ).
IDQ recently released a comprehensive and field-proven quantum-safe key exchange platform, Clarion KX, to manage hybrid cryptography on the network and facilitate large scale deployments of integrated quantum-safe networks. By hybridising PQC algorithm-based encryption and quantum physics-based communication security, Clarion KX ensures a highly secure quantum key distribution across Singtel’s QSN locations and provides enterprises with a cost-effective solution for long-term quantum-resilience of their core networks.
Earlier this year, Singtel also signed three Memoranda of Understanding with industry leaders, Cisco, Fortinet, and Nokia, so enterprises can easily deploy Cisco's routing platform, Fortinet's firewalls and Nokia's optical devices to boost their defences against advanced cyber threats.
Singtel’s QSN is part of its domestic network offerings which are built and engineered to secure business-critical data and provide enhanced security for the data network and flexibility as a managed service.
For more from Singtel, click here.
Simon Rowley - 11 November 2024
Cyber Security Insights for Resilient Digital Defence
Data Centre Security: Protecting Infrastructure from Physical and Cyber Threats
News
Integrity360 launches Managed dSOC Services
Integrity360, a pan-European cyber security specialist, today announced the launch of its Managed dSOC Services, an advanced security monitoring solution powered by Darktrace's AI-driven technology and Integrity360’s cyber security expertise.
The partnership allows Darktrace customers to gain access to an expert team dedicated to ensuring continuous, real-time monitoring, with around-the-clock expertise that internal teams may lack and to fully optimise and benefit from the capabilities of the platform.
The Managed dSOC Services are tailored to support businesses with proactive threat detection, rapid incident response, and continuous optimisation of their security investments, ensuring comprehensive protection against constantly evolving threats.
According to a recent report from Gartner, organisations that do not optimise and manage their cyber security solutions effectively may see a 30% increase in security incidents over the next three years. Integrity360’s Managed dSOC Service directly addresses this challenge by offering a fully managed service that takes the burden off internal teams, allowing businesses to focus on growth while ensuring optimal protection.
Eloina Pesce, Vice President of Channel, Darktrace, comments, “As organisations look to invest in AI-driven security tools like Darktrace, their internal teams may lack the time or skills to fully leverage them to their greatest benefit. Integrity360’s Managed dSOC fills a crucial gap for those organisations, helping them maximise their cyber security posture and reduce risk.
“Not only that, but Integrity360 experts build on the Darktrace ActiveAI Security Platform’s AI-driven detection and response with tailored services like proactive threat hunting and enhanced breach monitoring to provide an even greater level of protection.”
For Integrity360’s Darktrace customers, Integrity360’s Managed dSOC Services represent a critical enhancement to their cyber security investment. Darktrace’s platform, powered by advanced AI, offers unparalleled threat detection and real-time security insights. Augmenting this with Integrity360’s service capacity and expertise to fully manage the system will help organisations harness the platform’s full potential. Companies with a managed service like Managed dSOC will experience enhanced security optimisation, increasing further their return on investment from their Darktrace platform.
Integrity360’s Managed dSOC enables customers to fully capitalise on the benefits of their Darktrace investment, from 24/7 active monitoring to bespoke reporting and continuous AI model optimisation, ensuring clients not only detect threats in real time but also respond swiftly and strategically. With Integrity360’s specialised support, organisations can rest assured that their Darktrace environment is optimally configured, continually adapting to emerging cyber threats, and delivering maximum risk reduction.
“Through our partnership with Darktrace, we’re bringing an unmatched level of expertise and proactive support to our clients, allowing them to unlock the full potential of their cyber security investment,” says Brian Martin, Director of Product Management at Integrity360. “Nobody else can extract the same level of value out of the investment that we can, with this level of service and expertise underpinning it 24x7. Our Managed dSOC service suite brings this additional value within reach of all organisations irrespective of size, resources, or skill levels.”
The Managed dSOC service goes beyond traditional security operations by not only managing day-to-day monitoring, but also providing ongoing tuning and optimisation, incident support, and threat analysis to keep clients’ defences agile and aligned with current threats.
Integrity360’s Managed dSOC Services are available in three distinct tiers:• Managed dSOC: Core operational monitoring and breach detection, with daily reports for complete visibility and monthly health check• Managed dSOC+: Adds 24/7 active monitoring, high-value asset tagging, and periodic threat reviews for a more robust approach to security• Managed dSOC + MDR: Delivers advanced capabilities including threat response and proactive threat hunting
These flexible options allow businesses to select the level of support they require, from foundational monitoring to advanced threat detection and response, ensuring scalability as needs evolve.
Cyber security requires rigorous oversight and constant adaptation to new risks and Integrity360’s Managed dSOC Service addresses a prevalent universal challenge for most organisations: the cyber security skills and resource gap. Integrity360’s dedicated team of Darktrace experts ensures that every deployment is tailored to the client’s specific needs, refining configurations and implementing high-value security protocols to reduce exposure and enhance incident management.
As threats like ransomware, advanced phishing attacks, and supply chain compromises continue to surge, Integrity360’s Managed dSOC Services offer an essential service for companies seeking to strengthen their security posture while mitigating the complexity associated with managing AI-driven solutions. Managed dSOC Services represent a critical tool for businesses in high-risk sectors such as finance, healthcare, retail, government, and more, providing a comprehensive solution that combines advanced AI capabilities with expert oversight. By maximising the potential of Darktrace, organisations can minimise risk and confidently protect their critical assets.
Simon Rowley - 6 November 2024
Cyber Security Insights for Resilient Digital Defence
News
Aspire completes acquisition of CloudCoCo
Aspire Technology Solutions, a provider of managed IT, cyber security, and modern workplace technologies, has announced the acquisition of CloudCoCo, an experienced managed service provider headquartered in Leeds.
The acquisition marks a strategic advancement in Aspire’s plan to expand its UK presence and further strengthen its ability to deliver managed IT services, robust security solutions, and integrated modern workplace technology to clients across multiple industries, from SME to enterprise.
Building on Aspire’s successful acquisition of Cloud Cover IT in January 2024 - which expanded its footprint in Scotland and strengthened its service capabilities - CloudCoCo’s established relationships, skilled team, and expertise in managed IT, cloud, and unified communications will enable the Aspire Group to provide more tailored, responsive services that address the evolving needs of businesses across sectors. The acquisition will bring over £10 million in additional revenue and approximately 300 new customers to Aspire, setting the stage for future growth.
Chris Fraser, Aspire CEO and Founder, comments, “While CloudCoCo has undergone a period of structural transition, what truly stood out to us was its strong relationships with its high-quality customer base and the expertise within its team. These strengths align perfectly with our commitment to delivering technology like no other.
“This acquisition not only broadens our reach, but also enhances our ability to offer responsive, innovative solutions that meet the evolving needs of our clients. The CloudCoCo team will be an important part of Aspire’s next chapter, and together, we’re ready to make an even greater impact across key UK regions”.
Darren Weston, Group Operations Director at CloudCoCo, adds, “Joining Aspire represents an exciting new phase for CloudCoCo. We look forward to working closely with Chris and the team to expand our reach, deliver added value, and provide a wider range of innovative solutions. Aspire’s commitment to excellence aligns well with our own; it’s a powerful collaboration with a trusted UK technology provider that shares our values and goals.”
Aspire’s recent £1.7 million reinvestment in its established technology stack, as outlined in its FY24 accounts, reinforces the capabilities of its next-generation Security Operations Centre (SOC) and other critical infrastructure. Supported by LDC, a leading private equity firm known for backing high-growth UK businesses, this underscores Aspire’s dedication to driving innovation and maintaining the highest standards of service.
With an expanded presence across Gateshead, Glasgow, London, Stockton, and now Leeds, Aspire is seeking to set new benchmarks in managed IT, cyber security and modern workplace solutions for businesses throughout the UK.
For more from Aspire, click here.
Simon Rowley - 4 November 2024
Data
Data Centre Security: Protecting Infrastructure from Physical and Cyber Threats
News
Keepit scoops accolades at Infosec Innovator Awards
Keepit, a global provider of a comprehensive cloud backup and recovery platform, triumphed in four categories at the Top Infosec Innovator 2024 Awards, which took place at the recently-held CyberDefenceCon in Orlando, Florida.
Keepit was named the winner in the following categories: Cutting Edge Cloud Backup; Most Innovative Cyber Resilience; Hot Company Data Security Platform; and Hot Company Ransomware Protection of SaaS Data.
Headquartered in Copenhagen, Denmark, with offices and data centres globally, Keepit future-proofs cloud data for organisations, ensuring business continuity and access to information.
Michele Hayes, CMO at Keepit, comments, “Ransomware is only one of the many threats companies face in today’s cyber security landscape. Keepit provides the tools for companies to be secure and confident in their disaster recovery plans: a platform that enables rapid recovery and data monitoring for early anomaly detection. We’re thrilled that Cyber Defense Magazine has recognised our platform for these coveted awards.”
For more from Keepit, click here.
Simon Rowley - 4 November 2024
Data Centre Security: Protecting Infrastructure from Physical and Cyber Threats
News
Scality introduces RING XP storage software
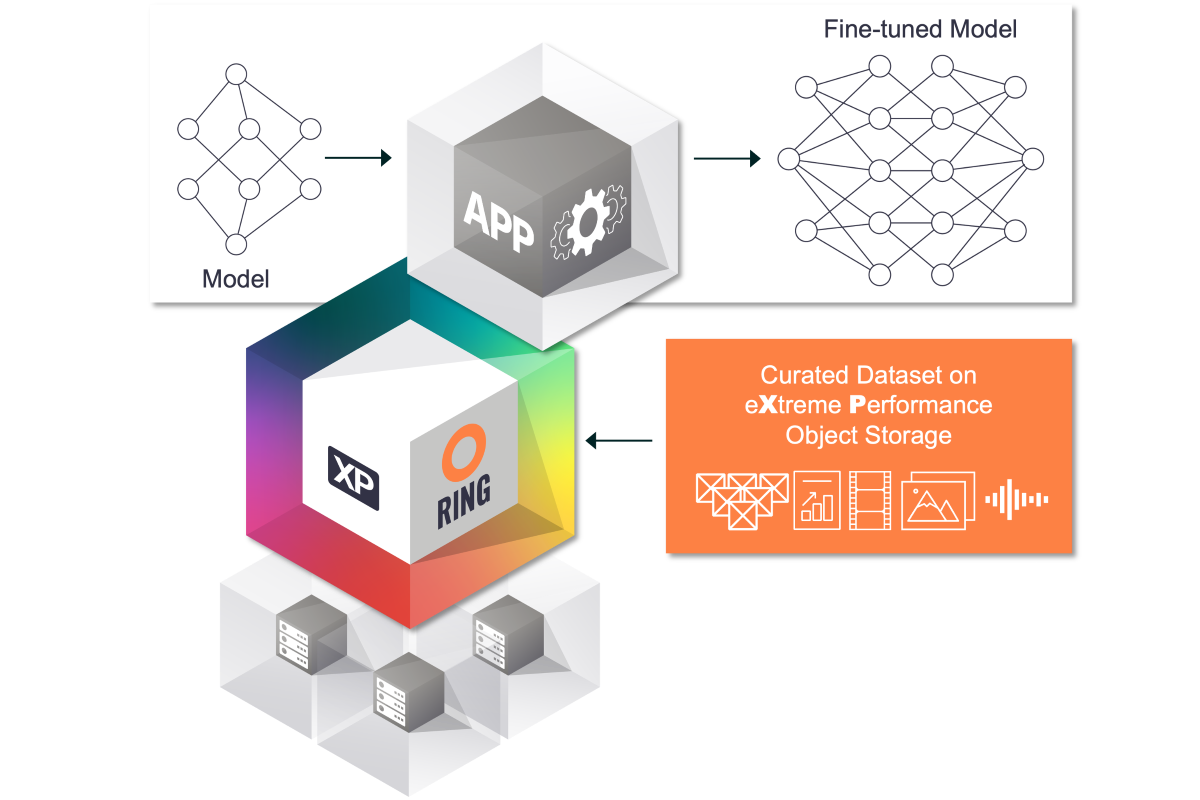
Scality, a developer of cyber-resilient storage software for the AI era, has unveiled RING XP, a new all-flash configuration of its RING storage software engineered for extreme performance. The company states that RING XP is now the fastest object store with microsecond response-time latencies for small object data, making it ideal for AI model training and fine-tuning.
Scality claims that RING XP is 10 to 20 times faster than Amazon S3 Express One Zone, and 50 to 100 times faster than Amazon S3 in terms of latency (milliseconds compared to microseconds). It is reportedly the first software-defined object storage solution to perform at levels previously only available from most costly, proprietary, hardware-based all-flash file systems and block arrays - but with the inherent advantages in scalability, simplicity, API access, security and cost provided by object storage.
Scality RING was recently ranked as number one on the 2024 GigaOm Radar for Enterprise Object Storage - achieving the highest scores across Key Features, Emerging Features and Business Criteria categories, and ahead of 17 competing vendors. RING already delivers scale-out, high-throughput capabilities used by hundreds of enterprises and service providers worldwide to power their critical business workloads.
“We have evolved the world’s most comprehensive and flexible object store and made it the world’s fastest,” says Giorgio Regni, CTO and Co-Founder of Scality. “Organisations globally have been looking to maximise how AI delivers value for their business. Object storage is a natural foundational repository for exabytes of data across the AI pipeline. With RING XP, we’ve not only optimised object storage for extreme performance but also reduced data silos - offering one seamless flexible technology for both long-term data retention and ultra-high performance AI workloads.”
To take object storage performance to a new level of microsecond response-time latencies, RING XP is based on:
• AI-optimised RING XP object storage connectors to provide scale-out, fast access to storage from applications• A performance-tuned RING storage software that accelerates storage I/O throughout the stack• AMD EPYC-based all-flash NVMe storage servers from Lenovo, Supermicro, Dell and HPE. EPYC provides industry-leading support for PCIe and NVMe, and the highest number of cores in single-socket CPUs to deliver optimal latencies
By achieving microsecond-level write (PUT) and read (GET) latency for 4KB objects, RING XP delivers performance to make it the ideal fast object storage target for AI tools, custom-developed applications, and performance-optimised file systems used for training AI models. Additional details on how RING XP attains microsecond latencies - considered the world’s fastest for object storage - are documented in the company's Solved blog.
RING XP, together with RING, delivers an end-to-end AI data pipeline storage management solution, designed to optimise and accelerate emerging AI-enabled business processes. Unlike traditional storage solutions that address only fragments of the AI workflow, RING XP and RING provide a unified platform that supports every stage of the AI pipeline - from ingesting massive datasets to model training, inference, and beyond.
The solution provides:
• RING as the foundational repository for AI data lakes with warm/cool/cold data at exabyte scale• RING XP for the extreme low-latency requirements of AI training data sets• Integrated lifecycle management for all phases of the data pipeline• Managed through a common framework of management and monitoring tools• End-to-end cyber-resiliency through integrated CORE5 capabilities to ensure security and data privacy
For more from Scality, click here.
Simon Rowley - 1 November 2024

Head office & Accounts:
Suite 14, 6-8 Revenge Road, Lordswood
Kent ME5 8UD
T: +44 (0)1634 673163
F: +44 (0)1634 673173