Security
Security
Are you a smart office? A risk assessment is the smartest thing you can do
The number of businesses using connected technology and the Internet of Things (IoT) is growing at a fast pace. These days, most organisations are using some kind of IoT technology in their day-to-day operations. Improved connectivity provides businesses with almost unlimited benefits, from greater efficiency, lower overheads and greater potential for profitability. However, it also introduces new avenues for cybersecurity attacks. The cost of connectivity is that attackers with nefarious intentions are looking to exploit vulnerabilities in IoT technology. That’s why it’s imperative to conduct a risk assessment.
Assessing risk in your organisation is a continuous process of discovering vulnerabilities and detecting threats—from the individual, to individual devices, applications, sites, data networks and the organisation as a whole.
In an ever-evolving cybersecurity threat landscape, security is not a one-time action. Conducting a holistic risk assessment allows for current and future-forward risk mitigation. A good risk assessment includes up-front technical measures along with ongoing practices that enable organisations to evaluate their cybersecurity risks and establish actions and policies that minimise threats over time. Along with finding vulnerabilities, it’s equally important to prepare staff and equip the organisation with processes and practices to respond quickly and efficiently as soon as a vulnerability is discovered.
Security should come standard with your data network
With a virtually impenetrable IoT network, you can build in defence by default.
Zero trust is a must
Your data network should use a zero trust model to ensure that unknown entities are not able to gain any access. By design, devices and users are not automatically trusted. Instead, the system constantly checks users and devices when they try to gain access to any data, at both a network and device level.
End-to-end encryption
End-to-end encryption (E2EE) prevents third parties from accessing data while it's being transferred from one end device or system to another. With E2EE in place, only the intended recipient can decrypt the data being transferred. Along the way, it’s secured against any tampering from any entity or service.
Smarter Technologies owns the private Orion IoT Data Network, the world’s first fully end-to-end IoT low-power radio network solution. This unique and proven system was developed alongside a long-standing involvement in the tracking and recovery of high-value assets such as cash in transit.
Smarter Technologies conducted a cyber risk assessment for the Financial Conduct Authority (FCA), a financial regulatory body in the United Kingdom.
The FCA receives information from many sources, including the Met Police, City of London Police and I-IMRC. These information partners required significant assurances that sensitive information shared would be appropriately secured; otherwise, they would stop sharing information with the FCA.
The FCA were planning to move their business intelligence and information storage to a cloud-based platform. They required assurances as to the risks associated, as well as a secure migration strategy.
Smarter Technologies conducted a full vendor-agnostic IS1&2 Risk Assessment complete with treatment plan, development of a security strategy and ethical phishing roadmap. A specific cloud security assessment fed into the cloud security strategy. The key findings from both of these deliverables were detailed in a report for key stakeholders to discuss the findings and implement a risk mitigation strategy.
A Safer Future for a Connected World
The world continues to be more connected than it has ever been. A holistic, and ongoing focus on cybersecurity is a requirement, not a nice-to-have. Defending against the IoT threats of today and tomorrow requires continual risk assessment to secure your IoT solutions. As the threat landscape evolves, so must you. Partnering with an expert in risk management empowers your organisation to manage risk so that you can focus on harnessing the true business value of your IoT solutions and products.
Beatrice - 1 March 2022
Security
LambdaTest announces integration with Datadog
LambdaTest has announced an integration with Datadog, the monitoring and security platform for cloud applications. This integration is now available in the Datadog Marketplace.
With the LambdaTest and Datadog integration, users can purchase a subscription to LambdaTest through the Datadog Marketplace. Once the LambdaTest account is set up (or existing customers of LambdaTest), users can now go to the integration tile to start sending data into Datadog. In addition, users can log bugs while performing cross-browser testing of websites (and web apps) from the LambdaTest platform to Datadog. LambdaTest will automatically include test run details like testing environment, browser version, OS, resolution, screenshots, as well as add custom comments.
“Since our inception, we have consistently worked towards ensuring that LambdaTest platform remains a part of the integrated testing ecosystem. Developers and testers use multiple tools to do their jobs and it’s important that these tools talk with each other. This new integration, which is now part of the 120+ integrations stable of LambdaTest, will enable smooth issue reporting and collaboration among testing and development teams. We will continuously look to increase our integrations in the times to come to ensure ease of work for our end-users,” says Asad Khan, CEO, LambdaTest.
“We’re excited to partner with LambdaTest for their offering on the Datadog Marketplace,” comments Michael Gerstenhaber, Senior Director of Product Management at Datadog. “Offering LambdaTest’s integration will enable seamless incident management for users, so that they can send any bug reported on LambdaTest directly to the Datadog incident dashboard easily and without added steps.”
LambdaTest offers automation testing on a scalable, secure, and reliable cloud grid. Users can test builds continuously on its cloud infrastructure for fast and comprehensive feedback. Users can cut commit-to-deploy time by 10x with parallel test execution and can even debug on the go.
Beatrice - 1 March 2022
Security
Charter of Trust and Digital Trust Forum join forces for greater cyber security
The Charter of Trust (CoT) and the Digital Trust Forum (DTF) are to join forces and merge under the Charter of Trust banner to form a joint initiative for greater cyber security and digital trust. With this the Charter of Trust also intends to devote more attention to the topic of trustworthy artificial intelligence in the future. The CoT was launched at the Munich Security Conference in February 2018 by Siemens and eight partners from the industrial sector. The DTF was formed in Berlin in May 2019 as an initiative of Bosch. With that Bosch will also join the CoT. The world’s leading logistics company Deutsche Post DHL Group has decided to join the cyber security initiative in addition, bringing the number of Charter of Trust members up to 17 four years after it was first signed.
"Overcoming reservations and building up trust will be crucial success factors in digital business – and this is more effective with the two initiatives working together. In addition, Bosch brings to the Charter of Trust its deep expertise in artificial intelligence," says Dr. Tanja Rückert, Chief Digital Officer at Robert Bosch GmbH and a new member of the Charter of Trust's Board of Directors.
"Cyber security is the key to building people's confidence in digitalisation," comments Cedrik Neike, Member of the Managing Board of Siemens AG and CEO Digital Industries. "And we're significantly stronger if we work together to make our networked world more resilient. By merging the two initiatives, and by bringing on board our new partners, the Charter of Trust will gain even greater diversity and broaden its perspective to cover different industries and countries."
“As a company, we inherit a long tradition of secure and fast transport of confidential information. But for us as a company, privacy of letters no longer applies exclusively to the postal service. In the digital environment, we also effectively protect our customers' information along the entire supply chain. By becoming a new member of the Charter of Trust, we want to embrace exchange on supply chain security, because ultimately security incidents may have severe implications on all parties involved,” says David Thornewill, Group CISO of Deutsche Post DHL Group.
Over the last four years, the Charter of Trust has already launched a wealth of measures to enhance cyber security – including "Security by Default", which takes cyber security into account right from the design phase and provides products with preconfigured security measures. In addition, the CoT partners have defined established baseline requirements for their suppliers in order to further enhance cyber security along supply chains. The main focus in the next phase will be to implement a cross-industry approach to the evaluation of supply chain security. In this context, the growing Charter of Trust community will provide mainly small and medium-sized enterprises with information, training and other resources.
The CoT initiative also collaborates regularly with various global authorities and scientific institutions to drive forward the topic of cyber security internationally and achieve harmony across national borders and organisational boundaries. Furthermore, the CoT initiative has created the Associated Partner Forum, which institutions such as Germany’s Federal Office for Information Security (BSI), the Spanish National Cryptologic Center (CCN), TU Graz and the Hasso Plattner Institute for Digital Engineering GmbH (HPI) have joined. The Canadian Centre for Cybersecurity, Cyber Readiness Institute, CyberNB, Cyber Peace Institute, Global Cyber Alliance and Japan's Ministry of Economy, Trade & Industry (METI) and Ministry of Internal Affairs and Communication (MIC) have also recently signed up as associate partners.
At the Munich Security Conference in February 2018, Siemens and eight partners from industry signed the world's first joint charter for greater cybersecurity. In addition to Siemens and the Munich Security Conference, the signatories include AES, Airbus, Allianz, Atos, Bosch, Dell Technologies, Deutsche Post DHL Group, IBM, Infineon Technologies AG, Mitsubishi Heavy Industries, NTT, NXP Semiconductors, SGS, TotalEnergies and TÜV SÜD.
The global economy is beginning to realise that increased networking goes hand in hand with an escalating risk of cybercrime: The Allianz Risk Barometer found that companies around the globe consider cyber risk as their number one threat in 2022.
Beatrice - 1 March 2022
Security
More data equals more risk – companies need to address data protection
This article was written exclusively for DCNN by AJ Thompson, CCO, Northdoor plc, on why companies need to prioritise data protection or risk making customer's data vulnerable to attack.
The last few years has seen both an explosion in the amount of data companies are collecting and also an increase in the level of public understanding about the value and vulnerability of their data.
All of this of course has caught the attention of cyber-criminals who are now searching for increasingly sophisticated methods to gain access to data. Today, companies face increasing pressure from regulators and the marketplace as a whole to improve how they collect, use, store and delete personal information, and how they manage data privacy.
More data but companies struggling to find ways to store it, protect it and use it
According to the Dell Global Data Protection Index, from September 2021, a survey of 1,000 IT decision makers from around the world found that companies are on average managing 10 times more data than they did in 2016. This is a huge increase in the amount of information entering companies. This offers opportunities to gain real insight into customers and business practices, which enables companies to have a proper understanding of how data can play an important role in future growth.
However, the more data you have the more complicated it is to store, protect and use. For example:
Cost: the more data you have, the more it costs to store and so finding the right storage option is critical to optimise budgets.
Reduced effectiveness: When a company has a large amount of data, it becomes much harder to process and identify the key data that might result on growth.
Compliance: More data doesn’t necessarily equate to more insight, and actually the ‘keep everything’ approach that many companies have followed now violates some of the new data regulations. With data protection agencies now fully enforcing GDPR with huge fines, companies have to be aware of what data they have, where it sits and how they use it.
Security: Finally, the more data a company has, the more difficult it is to secure and the greater the potential risk of a security breach.
Cyber criminals are finding increasingly sophisticated ways of gaining access to this data, selling it or holding it to ransom. This obviously causes considerable problems for companies who suffer data loss, damage to their reputation and potentially huge regulatory fines.
With so much more data residing within companies and cyber criminals determined and increasingly able to steal it, Dell’s Global Protection Index highlighted a disturbing admission from a majority of the companies it spoke to.
62% fear that their existing data protection measures may not be sufficient to cope with cyber threats.74% agreeing that the increase in employees working from home had increased their exposure to data loss.
These stats highlight what we have seen over the past few months. As cyber-crime has increased in regularity and sophistication, most businesses have been unable to keep up and as a result there has been a significant increase in successful attacks.
Another significant finding was that 82% of organisations believe that their existing data protection measures won’t be able to meet all future business needs. Whilst it is good that companies are recognising that they cannot stay still with their data protection, it seems that most don’t know where to turn next to resolve the issue.
It could be that they are looking for the wrong solutions, focusing just on traditional cyber defences. Cyber defence tends to be one step behind the cyber-criminal. No matter how high you build your defensive walls, cyber criminals will always find a way over the top to get at your data. Indeed, cyber-criminals are not just looking to get over the top of cyber defences, but through the backdoor. The last two years has seen a real increase in the number of attacks on organisations that have not originated with the organisation itself, but one of their partners. Attacks through the supply chain is an increasingly popular route for cyber-criminals which means companies need to get a 360-degree view of potential vulnerabilities across their network.
Whilst it’s important to have defences in place, looking at ways of protecting data that sit alongside cyber defence will be key for those worrying about future business needs.
Cyber resilience is key, not just cyber defence
Increasing your levels of cyber resilience will be critical in securing data. The connectivity of modern systems means that once criminals have gained access to them, they are able to access vast amounts of data relatively easily. This often includes any data that a company has backed up immediately rendering any disaster recovery plans are immediately negated.
The key then, is to backup data in a completely separated system, meaning that if a cyber-criminal does gain access, backup data is safe. This is where air gaps play a critical role. Placing data in systems, that are completely separated from the rest of the infrastructure, means that it is impossible for cyber-criminals to get their hands on it.
This level of cyber resilience means that data is in a fully isolated, highly secure and air gapped vault. Even if the worst happens and a breach impacts a company and its data backups, criminals are unable to get hold of the air gapped data and advanced workflows and tools will enable companies to recover quickly and securely.
Building cyber resilience through zero-trust
Another aspect of increasing cyber resilience within organisations is implementing a zero-trust approach. It is a security framework that requires all users (whether they are in or outside an organisation’s network) to be continually authenticated, authorised and validated before they are allowed near or access to data.
By taking a zero-trust approach, companies can be sure that some of the most sophisticated methods cyber-criminals are now using can be successfully identified and dealt with. It means that employees are constantly on the lookout for suspicious activity and ensures that a culture of good cyber security practice is implemented throughout a business.
This approach means that cyber-criminals don’t just have to get through the cyber defences but also a human wall and technology that are both running a zero-trust policy. By taking tis holistic approach to cyber security companies are able to apply layered security to every user, device, application, data base and access point. It also provides a clear view of present and future risk, often using Artificial Intelligence (AI) to triage threats.
Perhaps most importantly, it does all of this whilst balancing risk and productivity. It allows a company to continue operating, but wraps layered proactive AI-powered security around every user and every element inside its infrastructure.
It is clear that cyber-criminals are increasing the regularity and levels of sophistication of their attacks. Companies are aware of the increased threat but have reached a point when continuous spending on cyber defences, although important, no longer keeps criminals at bay. The definition of insanity is doing the same thing over and over again and expecting a different result – therefore finding new ways of protecting data and making it harder for the cyber-criminal to gain access to it is crucial.
Increased cyber resilience with air gap, siloed backups along with a zero-trust approach will help companies increase their security, protect their data and have a more future proofed solution in place to deal with an ever increasing threat.
Beatrice - 1 March 2022
Security
Is your lighting compromising your data security?
If you’re in the business of data, you’ll know that it’s a valuable asset that must be protected. You’ll also be acutely aware that wherever there is data, there is risk, and not just to your data alone. Physical security – the protection of people, property and assets should also be considered for their potential vulnerabilities.
While data centres are famously secure, ‘six layers deep’ in some cases, data theft still occurs. With a number of high-profile cases in the media, questions have been rightly raised over cybersecurity in the Internet of Things (IoT) and unfortunately, lighting and lighting control systems are not immune.
We ask Steve Mansell, Divisional Director of Critical Facilities for Zumtobel Group, how building services, such as lighting and controls, could be increasing your risk.
The potential threats
Data centre operators have come to expect that the products installed within their data hall meet certain criteria. Equipment should save energy, be sustainably sourced, but most of all, be safe and secure. However, technology is not without its vulnerabilities; we have all heard ‘that case’ with regards to ‘sub-standard’ data centres, security breaches and spying. As more things become connected, new levels of exposure are being discovered.
Considerations for a connected lighting system
Physical security
It is important to note that connected (wired) lighting systems without an IP address only communicate within your building. They pose a relatively low-security risk because a person has to be in the facility to attack the system. For example, a conventional wired DALI lighting control system could only be breached if the attacker physically connected to the network.
Device-to-device security
Lighting and control systems in a wireless network communicate outside of the building. It is common practice to use encryption, which means only devices with the correct ‘key’ can communicate with your system. Correct commissioning is therefore vital.
We know for some businesses, the fear of the unknown makes them reluctant to embrace and invest in new technologies through the fear of being exposed to potential attacks. They instil a culture of “if it’s not broken, it doesn't need to be fixed”, but with cyber-attacks increasing in sophistication, there is every reason to be more vigilant. After all, an ounce of prevention is worth a pound of cure.
This paper has therefore been designed to help data centre operators, who work tirelessly to ensure they have the in-house cybersecurity knowledge and expertise to make sound investments, stay a step ahead of attackers.
The risks
As soon as systems get connected to the IoT (cloud) proper protocols need to be in place. Potential forms of attack on connected lighting systems might include vectoring, Distributed Denial of Service (DDoS) or sniffing.
DDos
A Distributed Denial of service attack is an attempt to make an online service unavailable to its users by temporarily or indefinitely disrupting services.
Vectoring
Occurs when there is a security breach that uses an unsecured system to gain access to other networked systems.
Sniffing
An attacker sees a packet (data) in transmission from one point to other systems that utilises protocols that are not encrypted. Because it’s not encrypted the information can be modified i.e. to turn off the lights or CCTV.
How to mitigate risks
When it comes to the physical building infrastructure ecosystem, there are many different facets that need to be considered before you can be assured that the product meets your security criteria.
When considering the threats, we recommend starting at the beginning: with a rigorous procurement process, including developing trusted supply chain partnerships.
For example, when a luminaire or control system is specified, are you aware of every component that goes into that product?
Do you know if the manufacturer makes all components themselves? Or, do they rely on third-party suppliers? If so, you’re placing an enormous amount of trust in a potentially unknown supply chain: leaving systems open to security risks and significantly affecting quality control standards.
Quality assurance
So, what is the answer?
We’d recommend always working with a single-source supplier who can evidence where their components have been sourced and who offers full transparency of their supply chain partners.
For example, the Zumtobel Group are in complete control of their entire value chain.
The Group comprises three core brands - Tridonic, Thorn and Zumtobel. Tridonic is a manufacturer of components and control gear used by manufacturers worldwide due to its reputation for quality. Fortunately for Thorn and Zumtobel lighting, having a sister company that specialises in components and control gear certainly has its advantages, since there is complete oversight on where their componentry is sourced. Every individual product that makes up a Thorn or Zumtobel luminaire is therefore carefully selected, tested, and secured through the use of intelligent software and hardware protocols. When the manufacturer controls its own supply chain, there is complete end-to-end traceability and accountability, mitigating potential external threats.
As part of the product selection, thorough testing of both hardware and software used in any connected lighting and controls system is highly advisable.
Futureproofing for tomorrow
There is also another advantage of working with fewer trusted supply chain partners.
Not only does consolidating manufacturers make it easier to combat security vulnerabilities, it can also allow for future add-on services to be integrated at a later stage.
For example, it might be a lighting trunking system when installed, but it can also be a flexible infrastructure for future digital services.
A lighting track system such as TECTON or TECTON IP from Zumtobel can provide a backbone for adding future monitoring services that can grow with the data centre’s needs. It is simply a case of integrating sensors to accurately record the data a facility is interested in monitoring. For example, heat, to ensure the optimum operating temperature within the facility. Instead of having to purchase/install a whole new system for thermal management within a facility, operators and their technical teams can liaise with Zumtobel to plan the required system upgrade, then the additional products/sensors can be fitted directly to the TECTON track without the need to power the system down.
Alternatively, if a new sensor is required to measure other variables such as air quality, occupancy and motion, it is easy to remove the original sensor and add on the new one without reconfiguring the entire infrastructure. This naturally saves a significant amount of money in the long term, making it a fully flexible and future proof solution.
Beatrice - 1 March 2022
Security
A new age of data centre security
This article was written by Amy Young, Sales Director at Custodian Data Centres on the new age of data centre security.
The last two years have, in many cases, shown MSPs and their partners that the security protocols they had in place to protect their customers were less than robust. As you read this, the latest review of the 2018 Network and Information Systems (NIS) regulations is taking place. Initially designed to protect national data infrastructures, the regulations are proposed to expand their remit to include MSPs and their partners.
According to the latest Global Threat 2022 Report from Crowdstrike, 62% of cybersecurity incidents detected were malware-free, illustrating a significant shift in attack vectors. However, ransomware continues to be a major component in malicious attacks, with PwC concluding that business leaders expect these attacks to increase by over 60% in 2022.
However, it’s the expansion of the threat perimeter that will deliver the most challenges to CTOs as they re-imagine their enterprises within a post-pandemic business landscape. For them, choosing MSPs and their partners with security top of the agenda is imperative to include composable and mesh cybersecurity architectures.
Named as the foundation of cybersecurity, data centres connect and integrate security services with their customers to create a holistic ecosystem that enterprises can use to secure every aspect of their business processes. This integration also ensures all remote workers have secure tools they can use with absolute confidence, providing consistent security and expertise.
Cyberattack incident responses are also a critical component of every business’s contingency planning. A lesson learnt from the pandemic is that more resilience and strategic planning is needed to avoid or mitigate unforeseen incidents in the future. As enterprises switch permanently to mass remote working, the dispersed geography that now defines many business structures need the support of dynamic service organisations who have developed new secure event-driven architectures.
Proactive security
Robust and comprehensive digital security is based upon well-defined protocols. Enterprises must work with data partners not only accredited with ISO 27001 and PCI DSS facilities, but who also take security extremely seriously, in order to protect their business. These are the basis for secure, optimised and resilient organisations.
Creating adaptive systems will have the twin advantage of meeting all the regulatory compliance and delivering on the ground practical cyberattack defences. MSPs are reliant on their data centres to rapidly evolve and adapt to provide these future-forward secure environments. As new threats are identified, their services expand, re-focus and implement automatic security protocols to protect users and their data.
Securing your future
The level and diversity of cyberattacks facing businesses of all sizes show little sign of abating. The Cybersecurity Breaches Survey from last year showed that two in five (39%) of companies reported a cybersecurity incident, with nearly a third (27%) being attacked weekly.
The threats facing businesses today and those they will face in the future, require a dynamic approach to cybersecurity and physical security. Data centre services must have a dynamic and flexible solution available to meet the changing needs of their clients.
Security systems must also be intelligent. The advent of AI (particularly machine learning) leads to a new breed of security services that can use massive datasets and offer business users predictive analytics to indicate potential security issues across their networks and infrastructure. These evolving services are particularly important as advanced persistent threats continue to rise.
It is, however, vital to also place cyber security within the context of the physical environment it inhabits. To have a truly 360-degree view of the threat landscape an enterprise faces, physical assets must also be protected. Data centres that use CCTV, biometric identification, and state-of-the-art systems to suppress fire and flood are now an essential part of a comprehensive security strategy.
In order to thrive post-pandemic, businesses need to be resilient and agile, this agility includes how they secure their assets and data. Optimised mission-critical data centres can deliver the comprehensive security enterprises and MSPs now demand in this ever-transforming digital landscape.
Beatrice - 1 March 2022
Security
Secon outlines the top 10 cyber security trends for 2022
With much of the UK workforce now heading back into the office following the easing of COVID restrictions, there still remains a large amount of people choosing to work remotely or splitting their time between the office and home. This work life shift means that businesses need to continue to be vigilant and address the multiple vulnerabilities that still linger. This is according to Andrew Gogarty, Chief Security Evangelist, Secon.
Andrew comments: ”Over the last two years, organisations have quickly pivoted to remote working and accelerated cloud adoption to support business continuity during the global pandemic. This anywhere access to business-critical data resulted in security gaps and created challenges in maintaining effective cyber security.
“As the reports of multiple breaches and ongoing ransomware threats continue, we believe that there are 10 core security risks businesses need to address throughout 2022. Accordingly we have developed a white paper that looks into those threats in detail and will give any IT department or CISO the vital armour needed against the cyber criminals.”
Ransomware
Ransomware continues to impact organisations and remains an ongoing concern. As a result, many organisations have matured their backup and recovery approaches over the last few years with a view of being able to recover their data and environments, should ransomware break through defences. This approach has helped affected organisations avoid paying ransom demands to recover their data. However, ransomware will continue to prevail as one of the greatest risks to organisations.
Cloud breaches
The cloud helps organisations improve agility through expedited application roll outs, leverage automations and integrations to simplify operations, and ultimately reduce costs to increase revenues. As cloud adoption continues to increase throughout 2022, Secon expects to see an increase in unauthorised access and data breaches due to avoidable security gaps presented by misconfigurations and human error.
Vulnerability exploits
The growth in zero-day exploits is likely to become a bigger problem for security operations teams to manage going forward. As a result, Secon expects to see an increased adoption of zero trust in 2022 to help organisations eliminate their attack surface, control access to their data, and prevent lateral movement of threats.
Increase in exact domain name impersonation phishing
Since it requires little effort for threat actors and an improved click rate, Secon anticipates an increase in the usage of exact domain impersonation phishing emails in 2022.
As more organisations move to a DMARC policy of ‘reject,’ Secon says we can expect to see an increase in lookalike domain phishing. Due to this, it’s recommended to continue with user awareness training to help users identify these types of emails.
Cyber skills shortage continues
Resource constraints can limit an organisation’s ability to reduce risk, detect and respond to cyber threats. Secon expects an increase in the number of organisations outsourcing security operations tasks in 2022. Most organisations will outsource for vulnerability management, detection and response to help improve their cyber resilience and enable constrained resources to focus on organisational priorities.
Insider threat
Disgruntled employees and accidental mistakes can cause data breaches. In 2021, the battle for insider threats reached a new level of complexity, with reports of ransomware gangs openly seeking insiders to assist them in infecting their company networks in exchange for generous commissions. Secon says it expects to see an increase in organisations leveraging user and entity behaviour analytics (UEBA) solutions in 2022 to improve their capability in detecting and preventing insider threat activity.
Supply chain attacks
The supply chain remains an attractive target for criminal actors. This places a need on organisations to extend their risk management activities out to their suppliers through 2022 and beyond. Secon expects to see more scrutiny in supplier cyber security questionnaires moving forward. Being able to demonstrate solid cyber security maturity will start to become a competitive advantage for many organisations.
The European Union Agency for Cybersecurity (ENISA) has boldly stated that strong security protection is no longer enough for organisations when attackers have already shifted their attention to suppliers.
State-sponsored activities
Cyber attacks are expected to play a greater role in global conflicts. With innumerable and untold covert cyber espionage skirmishes launched to grasp sensitive information and peek at government and defence infrastructures, government-funded hacking operations will continue into 2022 and beyond. Thereby, governments will likely be proposing cyber security policies to have counter measurement capabilities and will continue to educate organisations on improving cyber security resilience.
Fake news and misinformation
As numerous events start to come back, Secon says we can expect to see more fake news campaigns, troll and bot accounts, and rogue marketing distributed through social networking sites and emails.
Fake news and misinformation aren’t only a problem for the government; fake news is also used to lure victims to malicious websites. Misinformation can be weaponised by adversaries to cause disorder for their own agenda.
In addition, deep fakes are expected to make a greater impact in 2022, thanks to various apps, web3.0, and AR/VR technologies becoming more mainstream.
Cyber Insurance
More organisations will invest in cyber security insurance during 2022. We expect the process to go beyond a paper-based tick box exercise; an increase in checks and validations will be made by insurers to see how companies address cyber risk and vulnerabilities, along with their detection and response capabilities to minimise impact.
Andrew concludes: “2022 will be another eventful year full of vulnerability exploits, account takeover attacks, phishing, and ransomware. Therefore, 2022 should be seen as an opportunity to go back and review the pivot-related changes of the last few years to see how visibility and control can be maintained to reduce business risk from cyber attacks.”
Beatrice - 1 March 2022
Security
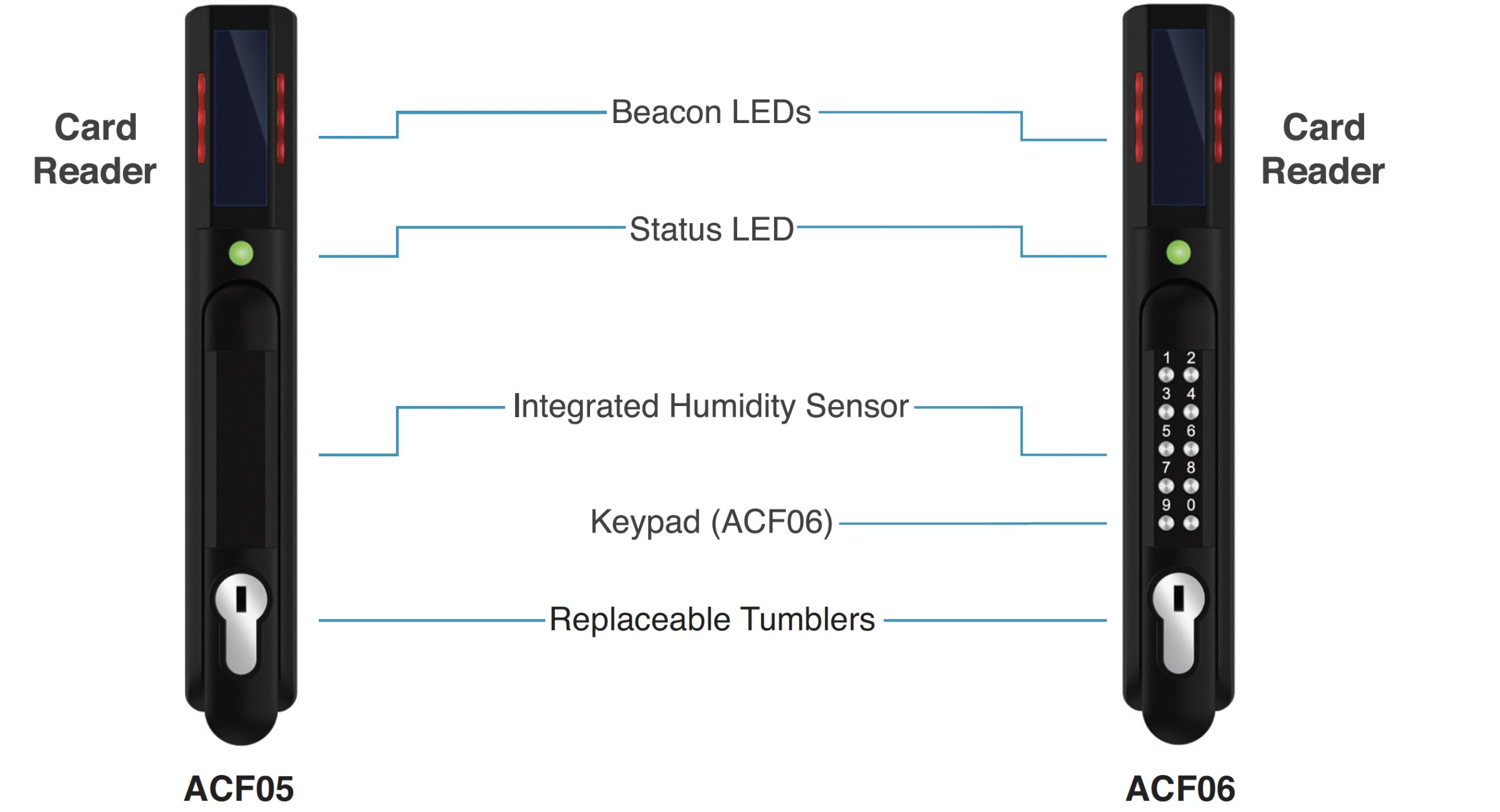
SmartZone G5 Security Handle offers secure dual authentication
Panduit has launched the SmartZone G5 Security Handle for ITE cabinets, which is designed to meet the most rigorous security challenges, both physical and digital, in today’s data centre environments. The multi-functional smart handle offers multiple configurations with and without a keypad to compliment users’ operational requirements. The integrated keypad version enables dual authentication by allowing for a card swipe and pin-code combination to access the cabinet.
The G5 Security handle seamlessly mates with most data centre cabinets and has the capability to read both low frequency (125kHz) and high frequency (13.5MHz) cards. The handle has been designed to be current and future compliant with regulations required within this environment and is also GDPR ready, HIPAA ready and PCI-DSS ready to ensure that this design meets data centres and users’ cabinet security needs.
It can support 200 authorised users and features an integral humidity sensor allowing humidity sensing to be optimally placed near the centre of the cabinet. The Status LED provides visual indication of the handle and security status. The Beacon LED is a visual indicator to provide status of the health of the cabinet at-a-glance. The beacon will flash yellow when the cabinet is in a minor alarm or flash red when the cabinet has a critical alarm. Users can use the beacon’s locate function to flash the beacon a defined colour to easily locate the cabinet when in a long run of cabinets.
Expanding the capabilities of the Panduit SmartZone software, the G5 Security handle offers an integrated humidity sensor and specially designed environmental and door sensors. This allows data capture and consolidation which is utilised for real-time monitoring management and automated documentation. The SmartZone G5 Security Handle connects directly to Panduit G5 iPDU and transmits real time information enabling control and management of cabinet access either directly through the on-board web interface or via SmartZone Cloud Software.
Beatrice - 1 March 2022

Head office & Accounts:
Suite 14, 6-8 Revenge Road, Lordswood
Kent ME5 8UD
T: +44 (0)1634 673163
F: +44 (0)1634 673173